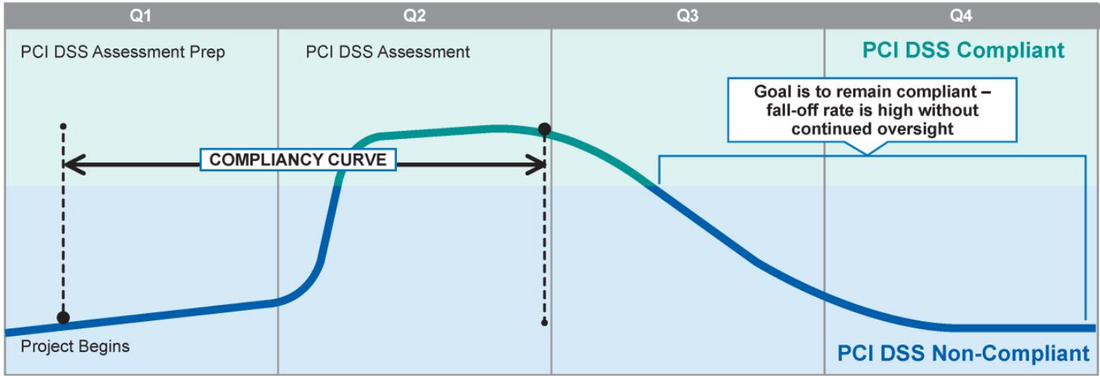
We should not delude ourselves. Getting seasonal compliance is indeed the aim/vision of a large part of the PCI community that sees in a PCI self-assessment or positive ROC, a business-enabler and/or penalties waiver. Of course, the state of their security controls will probably fall off in between two assessments and preparing (cleaning the mess) for their next audit could bel energy-consuming but who care? Not them. Mission completed!  When the cat's away the mice will play Research conducted by Verizon from 2011 through 2013 showed that many of the organizations that were assessed as being non-compliant at the time of their breach had successfully complied during their previous PCI DSS assessment and had lapsed back into non-compliance. The intend of PCI PCI expects organizations to maintain a continuous state of compliance throughout the year and not seeking point-in-time validation. The guidance for maintaining compliance For organizations that want to protect themselves and their customers from potential losses or damages resulting from a data breach, or just be in full compliance with the intend of PCI, the Council with the contribution of the community released the: Best Practices for Maintaining PCI DSS Compliance. Here are under 6 major rules extracted from this guidance. Golden rules for maintaining compliance Rule 1 - Commitment to Maintaining Compliance Executive sponsorship is critical if organizations want to be successful in implementing ongoing PCI DSS compliance programs. Rule 2 - Assign Ownership for Coordinating and monitoring security activities A compliance manager should be assigned overall responsibility for coordinating and monitoring execution of regular security activities such as patching systems, security-log reviews, wireless network scans, internal/external vulnerability scans and internal/external penetration tests are performed as required. Additionally, the compliance manager should be responsible for collecting, collating, and storing evidence to demonstrate ongoing PCI DSS security controls are operating effectively on a continuous basis. Rule 3 - Emphasize Security and Risk, Not Just Compliance Focus on building a culture of security and protecting an organization’s information assets and IT infrastructure, and allow compliance to be achieved as a consequence. Using risk as the basis for selecting security controls may allow an organization to tailor specific security controls differently to meet varying levels of organizational risk. 3.1 Use Risk to Balance Business Priorities with Security Needs Maintaining compliance with PCI DSS requires resources and financial investment. Using risk as the basis for measuring security effectiveness can make it easier for security teams to justify the expenditures necessary for building a comprehensive security and compliance program. 3.2 Integrate PCI DSS controls into a larger, common set of security controls defining a security framework adapted to your organization needs. When PCI DSS is integrated into an organization’s overall risk-based security framework, it makes it easier to incorporate specific PCI DSS activities into the normal day-to-day operations of the security team. This, in turn, helps to ensure these activities are conducted on a regular, ongoing basis, which can make maintaining PCI DSS compliance a much more manageable task. Rule 4 - Develop strategies to continuously monitor and document the implementation, effectiveness, adequacy, and status of all of your security controls. Develop processes for performing periodic reviews of all relevant security controls to confirm that:
Rule 5 - Detect and Respond to Security Control Failures It is critical that organizations are able to detect failures in security controls during the control-review or control-monitoring processes. It is also imperative that organizations have processes for responding to security control failures in a timely manner. In some cases, security control failures could constitute a formal security incident, and require a more formal incident response. Rule 6- Develop Performance Metrics to Measure Success Organizations should quantify their ability to sustain security practices and PCI DSS compliance by developing a set of metrics that summarize the performance of their security controls and security program. Risk reduction is a key metric for illustrating overall security-program effectiveness but metrics can provide meaningful indicators of security status at other levels within the security program as well. Rule 7 - Adjust the Program to Address Changes Have sound change-management practices to keep up with the changing threat landscape and to maintain ongoing compliance with PCI DSS. 7.1 Organization changes Failure to consider how such changes may impact the organization’s risk environment and/or PCI DSS scope could leave key business functions vulnerable to compromise or non- compliance. Examples of organization changes to consider: Merge, internal restructuring, corporate spin-offs, bankruptcies and liquidations, loss of key IT security personnel, and outsourcing arrangement 7.2 Changes in operational environment - network architecture or infrastructures - Organizations should evaluate how any changes to the operating environments might impact the scope or status of the organization’s PCI DSS compliance. Examples are: Deployment of new systems or applications, changes in system or network configurations, or changes in overall system topologies. 7.3 Changes in technologies Organizations should also review general technologies supporting the card data environment at least annually to confirm that they continue to support the security needs of the organization. Questions
Resources PCI: Are there benefits for Security? Funny but so True paper. PCI-GO Compliance Platform, a collaborative tool for Merchants and Auditing parties specifically tailored to reduce the cost and optimize the audit efforts PCI-GO Library: PCI DSS V3 policies, procedures and other templates ready to use PCI Best Practices for maintaining Compliance | |
Didier Godart
[email protected]
www.dgozone.com
+32498.78.77.44
LinkedIn: http://www.linkedin.com/in/didiergodart
[email protected]
www.dgozone.com
+32498.78.77.44
LinkedIn: http://www.linkedin.com/in/didiergodart
Find out how staff feels working for their employers with Myworkmood.com


 RSS Feed
RSS Feed
