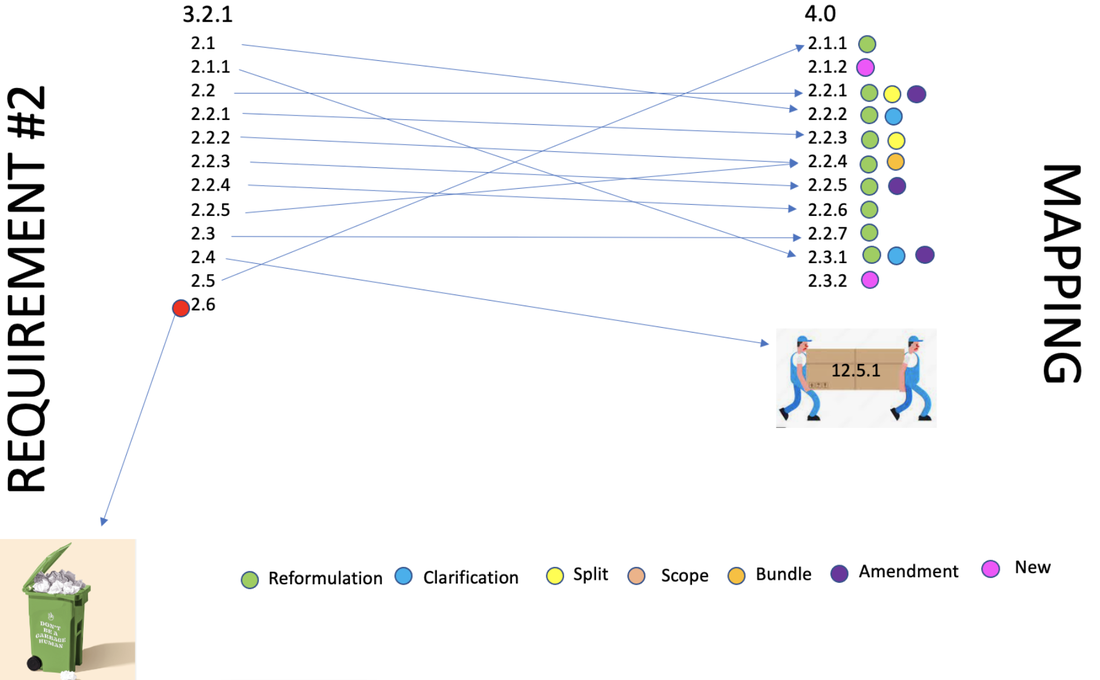
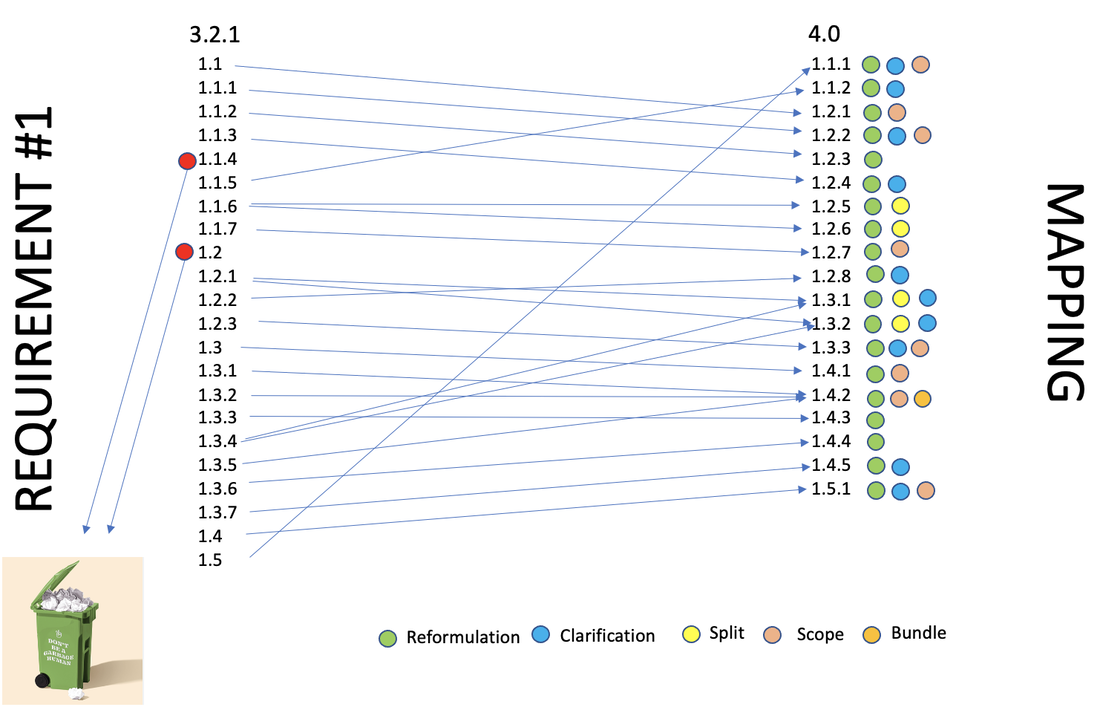
As a continuation to our previous articles discussing the impact of PCI DSS 4.0 on PCI DSS 3.2.1, we here below cover Requirement 3.
Overview
Change of terminologies:
5 controls have been added to this requirement:
Multiples controls have been amended to include the following controls:
One control of clause 12 has been moved and restated into requirement 3 (See detailed analysis)
Removed
None
- "The first 6 digits of a PAN" is replaced by "BIN".
- "Cardholder data" is replaced by "Account data"
5 controls have been added to this requirement:
- 4.0 - 3.1.2 Roles and responsibilities for performing activities in Requirement 3 are documented, assigned, and understood.
- 4.0 - 3.3.3 Additional requirement for issuers and companies that support issuing services and store sensitive authentication data: Any storage of sensitive authentication data is: Limited to that which is needed for a legitimate issuing business need and is secured. Encrypted using strong cryptography.
- 4.0 - 3.5.1.1 Hashes used to render PAN unreadable shall be keyed cryptographic hashes with associated key-management processes and procedures in accordance with Requirements 3.6 and 3.7. Note: This implies that organizations using SHA256 for instance for the hashing of PAN's need to use HMAC_SHA256 or similar.
- 4.0 - 3.7.9 Additional requirement for service providers only: Where a service provider shares cryptographic keys with its customers for transmission or storage of account data, guidance on secure transmission, storage and updating of such keys is documented and distributed to the service provider’s customers.
Multiples controls have been amended to include the following controls:
- The policies and procedures shall cover all locations of stored account data as well as sensitive authentication data (SAD) stored prior to completion of authorization.
- Disk -level encryption shall be implemented on removable electronic media OR If used for non-removable electronic media, PAN shall also be rendered unreadable. Authentication factors allowing access to unencrypted data are stored securely. Note: This stresses that that column and field-level encryption within the database is acceptable, but databases which encrypt the entire partition (disk) are prohibited. Organizations which rely on disk encryption to store and/or exchange files will need to implement file-level encryption to protect files on disk. Organization’s using Transparent Disk Encryption to protect database partitions will need to implement column-level encryption for columns which contain cardholder data.
- Cryptographic keys used in production and test environments shall be different.
- Inventory of cryptographic components shall cover key management systems (KMS)
- A defined cryptoperiod shall be documented or each key type in use.
One control of clause 12 has been moved and restated into requirement 3 (See detailed analysis)
Removed
None
PCI 4.0 Compliance Dashboard
Get your PCI 4.0 COMPLIANCE DASHBOARD TOOL . Fully aligned with PCI DSS V4.0. It includes the defined approach requirements, the customized approach, applicability notes, purpose, good practices & further information, definition, example and defined testing procedures and prioritization approach. It also provides templates to register your compensating controls, controls met with remediations but also to register your customized Controls, the outcome of the customized approach risk assessments and the risk assessments for the definition of frequency periods as well as to register execution of vulnerability scans and penetration tests.
Details Analysis
Titre
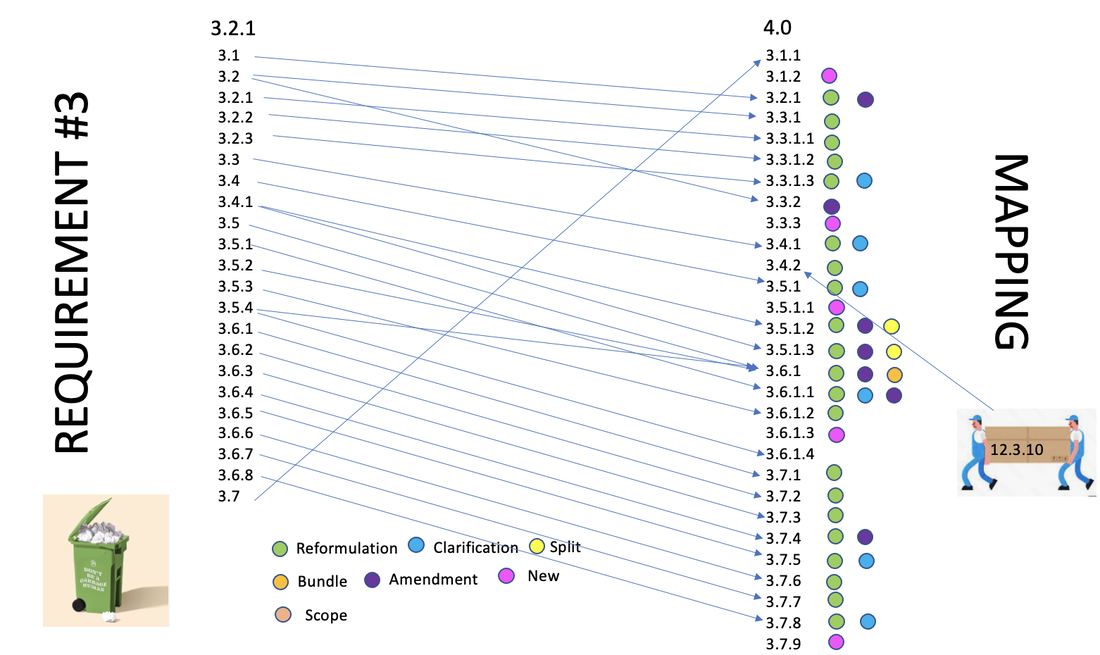
3.2.1 - Protect stored cardholder data / 4.0 - Protect Stored Account Data
3.2.1 - Protect stored cardholder data / 4.0 - Protect Stored Account Data
3.2.1 - 3.1 Keep cardholder data storage to a minimum by implementing data retention and disposal policies, procedures and processes that include at least the following for all cardholder data (CHD) storage:
Change: Reformulation + Amendments
4.0 - 3.2.1 Account data storage is kept to a minimum through implementation of data retention and disposal policies, procedures, and processes that include at least the following:
- Limiting data storage amount and retention time to that which is required for legal, regulatory, and business requirements
- Processes for secure deletion of data when no longer needed
- Specific retention requirements for cardholder data
- A quarterly process for identifying and securely deleting stored cardholder data that exceeds defined retention.
Change: Reformulation + Amendments
4.0 - 3.2.1 Account data storage is kept to a minimum through implementation of data retention and disposal policies, procedures, and processes that include at least the following:
- Coverage for all locations of stored account data.
- Coverage for any sensitive authentication data (SAD) stored prior to completion of authorization.
- Limiting data storage amount and retention time to that which is required for legal or regulatory, and/or business requirements.
- Specific retention requirements for stored account data that defines length of retention period and includes a documented business justification.
- Processes for secure deletion or rendering account data unrecoverable when no longer needed per the retention policy.
- A process for verifying, at least once every three months, that stored account data exceeding the defined retention period has been securely deleted or rendered unrecoverable.
3.2.1 - 3.2 Do not store sensitive authentication data after authorization (even if encrypted). If sensitive authentication data is received, render all data unrecoverable upon completion of the authorization process.
Change: Reformulation + Amendments
4.0 - 3.3.1 SAD is not retained after authorization, even if encrypted. All sensitive authentication data received is rendered unrecoverable upon completion of the authorization process.
4.0 - 3.3.2 SAD that is stored electronically prior to completion of authorization is encrypted using strong cryptography.
Change: Reformulation + Amendments
4.0 - 3.3.1 SAD is not retained after authorization, even if encrypted. All sensitive authentication data received is rendered unrecoverable upon completion of the authorization process.
4.0 - 3.3.2 SAD that is stored electronically prior to completion of authorization is encrypted using strong cryptography.
3.2.1 - 3.2.1 Do not store the full contents of any track (from the magnetic stripe located on the back of a card, equivalent data contained on a chip, or elsewhere) after authorization. This data is alternatively called full track, track, track 1, track 2, and magnetic-stripe data
Change: Reformulation
4.0 - 3.3.1.1 The full contents of any track are not retained upon completion of the authorization process.
Change: Reformulation
4.0 - 3.3.1.1 The full contents of any track are not retained upon completion of the authorization process.
3.2.1 - 3.2.2 Do not store the card verification code or value (three-digit or four-digit number printed on the front or back of a payment card used to verify card-not- present transactions) after authorization.
Change: Reformulation
4.0 - 3.3.1.2 The card verification code is not retained upon completion of the authorization process.
Change: Reformulation
4.0 - 3.3.1.2 The card verification code is not retained upon completion of the authorization process.
3.2.1 - 3.2.3 Do not store the personal identification number (PIN) or the encrypted PIN block after authorization.
Change: Reformulation + Clarification
4.0 - 3.3.1.3 The personal identification number (PIN) and the PIN block are not retained upon completion of the authorization process.
Change: Reformulation + Clarification
4.0 - 3.3.1.3 The personal identification number (PIN) and the PIN block are not retained upon completion of the authorization process.
3.2.1 - 3.3 Mask PAN when displayed (the first six and last four digits are the maximum number of digits to be displayed), such that only personnel with a legitimate business need can see more than the first six/last four digits of the PAN.
Change: Reformulation + Clarification
4.0 - 3.4.1 PAN is masked when displayed (the BIN and last four digits are the maximum numberof digits to be displayed), such that only personnel with a legitimate business need can see more thanthe BIN and last four digits of the PAN.
Change: Reformulation + Clarification
4.0 - 3.4.1 PAN is masked when displayed (the BIN and last four digits are the maximum numberof digits to be displayed), such that only personnel with a legitimate business need can see more thanthe BIN and last four digits of the PAN.
3.2.1 - 3.4 Render PAN unreadable anywhere it is stored (including on portable digital media, backup media, and in logs) by using any of the following approaches:
Change: Reformulation, Clarification
4.0 - 3.5.1 PAN is rendered unreadable anywhere it is stored by using any of the following approaches:
- One-way hashes based on strong cryptography, (hash must be of the entire PAN)
- Truncation (hashing cannot be used to replace the truncated segment of PAN)
- Index tokens and pads (pads must be securely stored)
- Strong cryptography with associated key-management processes and procedures.
Change: Reformulation, Clarification
4.0 - 3.5.1 PAN is rendered unreadable anywhere it is stored by using any of the following approaches:
- One-way hashes based on strong cryptography of the entire PAN.
- Truncation (hashing cannot be used to replace the truncated segment of PAN).
- Index tokens.
- Strong cryptography with associated key- management processes and procedures.
3.2.1 - 3.4.1 If disk encryption is used (rather than file- or column-level database encryption), logical access must be managed separately and independently of native operating system authentication and access control mechanisms (for example, by not using local user account databases or general network login credentials). Decryption keys must not be associated with user accounts.
Change : Reformulation + Amendments + Split
4.0 - 3.5.1.2 If disk-level or partition-level encryption (rather than file-, column-, or field-level database encryption) is used to render PAN unreadable, it is implemented only as follows:
4.0 - 3.5.1.3 If disk-level or partition-level encryption is used (rather than file-, column-, or field--level database encryption) to render PAN unreadable, it is managed as follows:
Change : Reformulation + Amendments + Split
4.0 - 3.5.1.2 If disk-level or partition-level encryption (rather than file-, column-, or field-level database encryption) is used to render PAN unreadable, it is implemented only as follows:
- On removable electronic media OR
- If used for non-removable electronic media, PAN is also rendered unreadable via another mechanism that meets Requirement 3.5.1.
4.0 - 3.5.1.3 If disk-level or partition-level encryption is used (rather than file-, column-, or field--level database encryption) to render PAN unreadable, it is managed as follows:
- Logical access is managed separately and independently of native operating system authentication and access control mechanisms.
- Decryption keys are not associated with user accounts.
- Authentication factors (passwords, passphrases, or cryptographic keys) that allow access to unencrypted data are stored securely.
3.2.1 - 3.5 Document and implement procedures to protect keys used to secure stored cardholder data against disclosure and misuse:
Change: Reformulation + Amendments
4.0 - 3.6.1 Procedures are defined and implemented to protect cryptographic keys used to protect stored account data against disclosure and misuse that include:
Change: Reformulation + Amendments
4.0 - 3.6.1 Procedures are defined and implemented to protect cryptographic keys used to protect stored account data against disclosure and misuse that include:
- Access to keys is restricted to the fewest number of custodians necessary.
- Key-encrypting keys are at least as strong as the data-encrypting keys they protect.
- Key-encrypting keys are stored separately from data-encrypting keys.
- Keys are stored securely in the fewest possible locations and forms.
3.2.1 - 3.5.1 Additional requirement for service providers only: Maintain a documented description of the cryptographic architecture that includes:
Change : Reformulation + Clarification + Amendment
4.0 - 3.6.1.1 Additional requirement for service providers only: A documented description of the cryptographic architecture is maintained that includes:
- Details of all algorithms, protocols, and keys used for the protection of cardholder data, including key strength and expiry date
- Description of the key usage for each key
- Inventory of any HSMs and other SCDs used for key management
Change : Reformulation + Clarification + Amendment
4.0 - 3.6.1.1 Additional requirement for service providers only: A documented description of the cryptographic architecture is maintained that includes:
- Details of all algorithms, protocols, and keys used for the protection of stored account data, including key strength and expiry date.
- Preventing the use of the same cryptographic keys in production and test environments.
- Description of the key usage for each key.
- Inventory of any hardware security modules (HSMs), key management systems (KMS), and other secure cryptographic devices (SCDs) used for key management, including type and location of devices, as outlined in Requirement 12.3.4.
3.2.1 - 3.5.2 Restrict access to cryptographic keys to the fewest number of custodians necessary.
Change: Reformulation + Merge
4.0 - 3.6.1 Procedures are defined and implemented to protect cryptographic keys used to protect stored account data against disclosure and misuse that include:
Change: Reformulation + Merge
4.0 - 3.6.1 Procedures are defined and implemented to protect cryptographic keys used to protect stored account data against disclosure and misuse that include:
- Access to keys is restricted to the fewest number of custodians necessary.
- Key-encrypting keys are at least as strong as the data-encrypting keys they protect.
- Key-encrypting keys are stored separately from data-encrypting keys.
- Keys are stored securely in the fewest possible locations and forms.
3.2.1 - 3.5.3 Store secret and private keys used to encrypt/decrypt cardholder data in one (or more) of the following forms at all times:
Change: Reformulation + Split/Shuffling + Redundancy
4.0 - 3.6.1 Procedures are defined and implemented to protect cryptographic keys used to protect stored account data against disclosure and misuse that include:
4.0 - 3.6.1.2 Secret and private keys used to encrypt/decrypt stored account data are stored in one (or more) of the following forms at all times:
- Encrypted with a key-encrypting key that is at least as strong as the data- encrypting key, and that is stored separately from the data-encrypting key
- Within a secure cryptographic device (such as a hardware (host) security module (HSM) or PTS-approved point-of-interaction device)
- As at least two full-length key components or key shares, in accordance with an industry- accepted method
Change: Reformulation + Split/Shuffling + Redundancy
4.0 - 3.6.1 Procedures are defined and implemented to protect cryptographic keys used to protect stored account data against disclosure and misuse that include:
- Access to keys is restricted to the fewest number of custodians necessary.
- Key-encrypting keys are at least as strong as the data-encrypting keys they protect.
- Key-encrypting keys are stored separately from data-encrypting keys.
- Keys are stored securely in the fewest possible locations and forms.
4.0 - 3.6.1.2 Secret and private keys used to encrypt/decrypt stored account data are stored in one (or more) of the following forms at all times:
- Encrypted with a key-encrypting key that is at least as strong as the data-encrypting key, and that is stored separately from the data- encrypting key.
- Within a secure cryptographic device (SCD), such as a hardware security module (HSM) or PTS-approved point-of-interaction device.
- As at least two full-length key components or key shares, in accordance with an industry-accepted method.
3.2.1 - 3.5.4 Store cryptographic keys in the fewest possible locations.
Change: Reformulation + Redundancy
4.0 - 3.6.1.4 Cryptographic keys are stored in the fewest possible locations.
4.0 - 3.6.1 Procedures are defined and implemented to protect cryptographic keys used to protect stored account data against disclosure and misuse that include:
Change: Reformulation + Redundancy
4.0 - 3.6.1.4 Cryptographic keys are stored in the fewest possible locations.
4.0 - 3.6.1 Procedures are defined and implemented to protect cryptographic keys used to protect stored account data against disclosure and misuse that include:
- Access to keys is restricted to the fewest number of custodians necessary.
- Key-encrypting keys are at least as strong as the data-encrypting keys they protect.
- Key-encrypting keys are stored separately from data-encrypting keys.
- Keys are stored securely in the fewest possible locations and forms.
3.2.1 - 3.6 Fully document and implement all key- management processes and procedures for cryptographic keys used for encryption of cardholder data, including the following:
Change: Split
4.0 - 3.7.1 to 3.7.8
Change: Split
4.0 - 3.7.1 to 3.7.8
3.2.1 - 3.6.1 Generation of strong cryptographic keys
Change: Reformulation
4.0 - 3.7.1 Key-management policies and procedures are implemented to include generation of strong cryptographic keys used to protect stored account data.
Change: Reformulation
4.0 - 3.7.1 Key-management policies and procedures are implemented to include generation of strong cryptographic keys used to protect stored account data.
3.2.1 - 3.6.2 Secure cryptographic key distribution
Change: Reformulation
4.0 - 3.7.2 Key-management policies and procedures are implemented to include secure distribution of cryptographic keys used to protect stored account data.
Change: Reformulation
4.0 - 3.7.2 Key-management policies and procedures are implemented to include secure distribution of cryptographic keys used to protect stored account data.
3.2.1 - 3.6.3 Secure cryptographic key storage
Change: Reformulation
4.0 - 3.7.3 Key-management policies and procedures are implemented to include secure storage of cryptographic keys used to protect stored account data.
Change: Reformulation
4.0 - 3.7.3 Key-management policies and procedures are implemented to include secure storage of cryptographic keys used to protect stored account data.
3.2.1 - 3.6.4 Cryptographic key changes for keys that have reached the end of their cryptoperiod (for example, after a defined period of time has passed and/or after a certain amount of cipher-text has been produced by a given key), as defined by the associated application vendor or key owner, and based on industry best practices and guidelines (for example, NIST Special Publication 800-57).
Change: Reformulation + Amendments
4.0 - 3.7.4 Key management policies and procedures are implemented for cryptographic key changes for keys that have reached the end of their cryptoperiod, as defined by the associated application vendor or key owner, and based on industry best practices and guidelines, including the following:
Change: Reformulation + Amendments
4.0 - 3.7.4 Key management policies and procedures are implemented for cryptographic key changes for keys that have reached the end of their cryptoperiod, as defined by the associated application vendor or key owner, and based on industry best practices and guidelines, including the following:
- A defined cryptoperiod for each key type in use.
- A process for key changes at the end of the defined cryptoperiod.
3.2.1 - 3.6.5 Retirement or replacement (for example, archiving, destruction, and/or revocation) of keys as deemed necessary when the integrity of the key has been weakened (for example, departure of an employee with knowledge of a clear-text key component), or keys are suspected of being compromised.
Change: Change: Reformulation + Clarification
3.2.1 - 3.7.5 Key management policies procedures are implemented to include the retirement, replacement, or destruction of keys used to protect stored account data, as deemed necessary when:
Change: Change: Reformulation + Clarification
3.2.1 - 3.7.5 Key management policies procedures are implemented to include the retirement, replacement, or destruction of keys used to protect stored account data, as deemed necessary when:
- The key has reached the end of its defined cryptoperiod.
- The integrity of the key has been weakened, including when personnel with knowledge of a cleartext key component leaves the company, or the role for which the key component was known.
- The key is suspected of or known to be compromised.
Retired or replaced keys are not used for encryption operations.
3.2.1 - 3.6.6 If manual clear-text cryptographic key-management operations are used, these operations must be managed using split knowledge and dual control.
Change: Reformulation
4.0 - 3.7.6 Where manual cleartext cryptographic key- management operations are performed by personnel, key-management policies and procedures are implemented include managing these operations using split knowledge and dual control.
Change: Reformulation
4.0 - 3.7.6 Where manual cleartext cryptographic key- management operations are performed by personnel, key-management policies and procedures are implemented include managing these operations using split knowledge and dual control.
3.2.1 - 3.6.7 Prevention of unauthorized substitution of cryptographic keys.
Change: Reformulation
4.0 - 3.7.7 Key management policies and procedures are implemented to include the prevention of unauthorized substitution of cryptographic keys.
Change: Reformulation
4.0 - 3.7.7 Key management policies and procedures are implemented to include the prevention of unauthorized substitution of cryptographic keys.
3.2.1 - 3.6.8 Requirement for cryptographic key custodians to formally acknowledge that they understand and accept their key- custodian responsibilities
Change: Reformulation + Clarification
4.0 - 3.7.8 Key management policies and procedures are implemented to include that cryptographic key custodians formally acknowledge (in writing or electronically) that they understand and accept their key-custodian responsibilities.
Change: Reformulation + Clarification
4.0 - 3.7.8 Key management policies and procedures are implemented to include that cryptographic key custodians formally acknowledge (in writing or electronically) that they understand and accept their key-custodian responsibilities.
3.2.1 - 3.7 Ensure that security policies and operational procedures for protecting stored cardholder data are documented, in use, and known to all affected parties.
Change: Reformulation
4.0 - 3.1.1 All security policies and operational procedures that are identified in Requirement 3 are:
• Documented.
• Kept up to date.
• In use.
• Known to all affected parties.
Change: Reformulation
4.0 - 3.1.1 All security policies and operational procedures that are identified in Requirement 3 are:
• Documented.
• Kept up to date.
• In use.
• Known to all affected parties.
3.2.1 - 12.3.10 For personnel accessing cardholder data via remote-access technologies, prohibit the copying, moving, and storage of cardholder data onto local hard drives and removable electronic media, unless explicitly authorized for a defined business need. Where there is an authorized business need, the usage policies must require the data be protected in accordance with all applicable PCI DSS Requirements.
Change: Move and reformulation
4.0 - 3.4.2 When using remote-access technologies, technical controls prevent copy and/or relocation of PAN for all personnel, except for those with documented, explicit authorization and a legitimate, defined business need.
Change: Move and reformulation
4.0 - 3.4.2 When using remote-access technologies, technical controls prevent copy and/or relocation of PAN for all personnel, except for those with documented, explicit authorization and a legitimate, defined business need.
3.2.1 - NONE
Change: NEW
4.0 - 3.1.2 Roles and responsibilities for performing activities in Requirement 3 are documented, assigned, and understood.
Change: NEW
4.0 - 3.1.2 Roles and responsibilities for performing activities in Requirement 3 are documented, assigned, and understood.
3.2.1 - None
Change: NEW
4.0 - 3.3.3 Additional requirement for issuers and companies that support issuing services and store sensitive authentication data: Any storage of sensitive authentication data is:
Limited to that which is needed for a legitimate issuing business need and is secured.
Encrypted using strong cryptography.
Change: NEW
4.0 - 3.3.3 Additional requirement for issuers and companies that support issuing services and store sensitive authentication data: Any storage of sensitive authentication data is:
Limited to that which is needed for a legitimate issuing business need and is secured.
Encrypted using strong cryptography.
3.2.1 - None
Change: NEW
4.0 - 3.5.1.1 Hashes used to render PAN unreadable are keyed cryptographic hashes of the entire PAN, with associated key-management processes and procedures in accordance with Requirements 3.6 and 3.7.
Change: NEW
4.0 - 3.5.1.1 Hashes used to render PAN unreadable are keyed cryptographic hashes of the entire PAN, with associated key-management processes and procedures in accordance with Requirements 3.6 and 3.7.
3.2.1 - None
Change: NEW
4.0 3.6.1.3 Access to cleartext cryptographic key components is restricted to the fewest number of custodians necessary.
Change: NEW
4.0 3.6.1.3 Access to cleartext cryptographic key components is restricted to the fewest number of custodians necessary.
3.2.1 - None
Change: NEW
4.0 - 3.7.9 Additional requirement for service providers only: Where a service provider shares cryptographic keys with its customers for transmission or storage of account data, guidance on secure transmission, storage and updating of such keys is documented and distributed to the service provider’s customers.
Change: NEW
4.0 - 3.7.9 Additional requirement for service providers only: Where a service provider shares cryptographic keys with its customers for transmission or storage of account data, guidance on secure transmission, storage and updating of such keys is documented and distributed to the service provider’s customers.
 RSS Feed
RSS Feed
