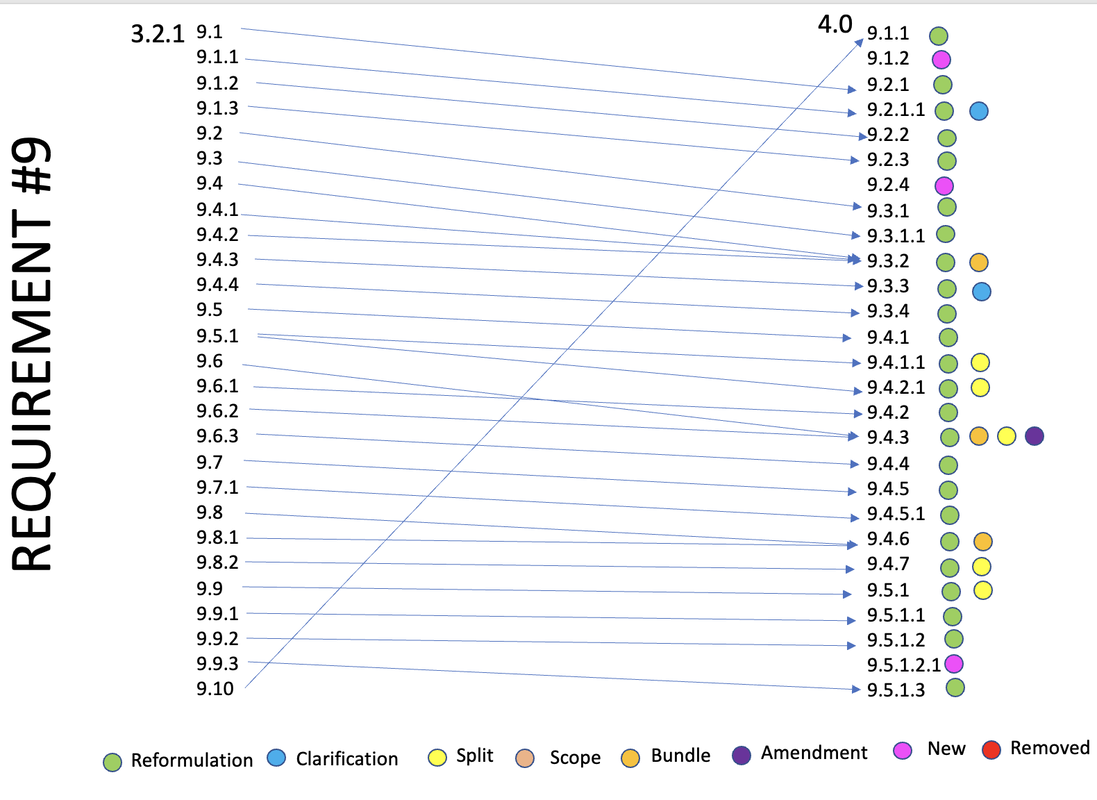
The impact of the new PCI 4.0 on the former 3.2.1 requirement 9 is in the form of: Reformulation, Clarification, Change/amendment, Merge and split.
Overview
Terminology:
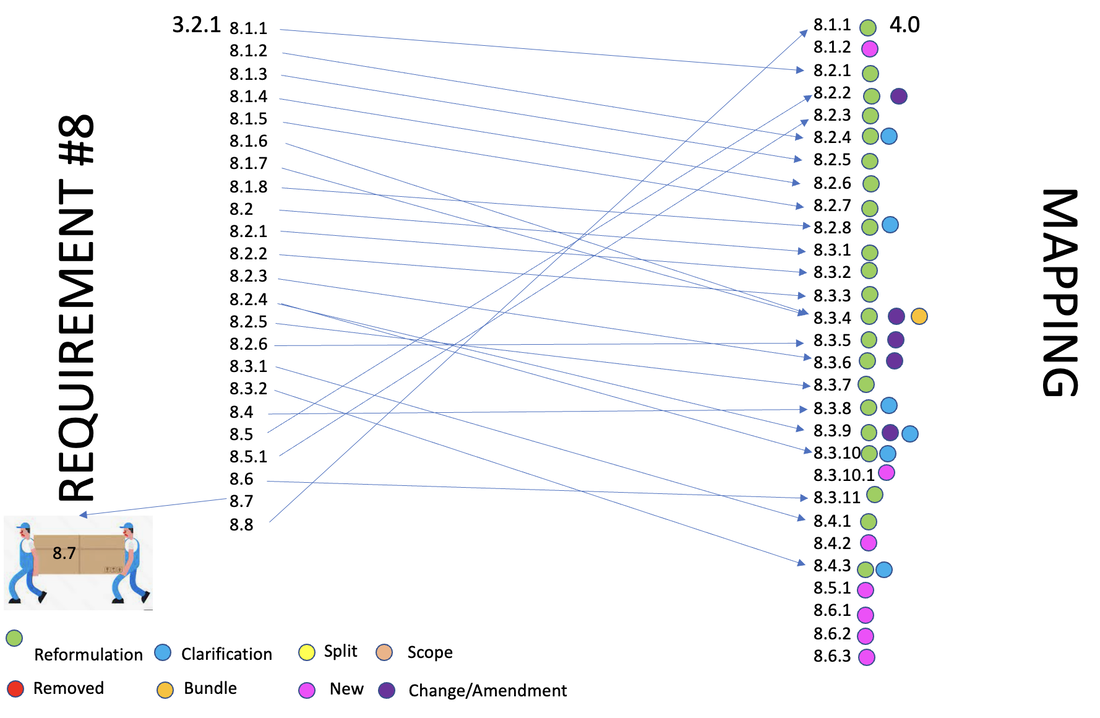
New controls: 3 new controls
4.0 - 9.5.1.2.1 Stating that the definition of the frequency of periodic POI device inspections and the type of inspections to perform shall be determined and documented in the entity’s targeted risk analysis.
4.0 - 9.1.2 Requires Roles and responsibilities for performing activities in Requirement 9 to be documented, assigned, and understood.
4.0 - 9.2.4 requires to lock consoles ijn sensitive areas when not in use.
Changes:
4.0 - 9.4.3 Requires to record/log the location to which media are sent out.
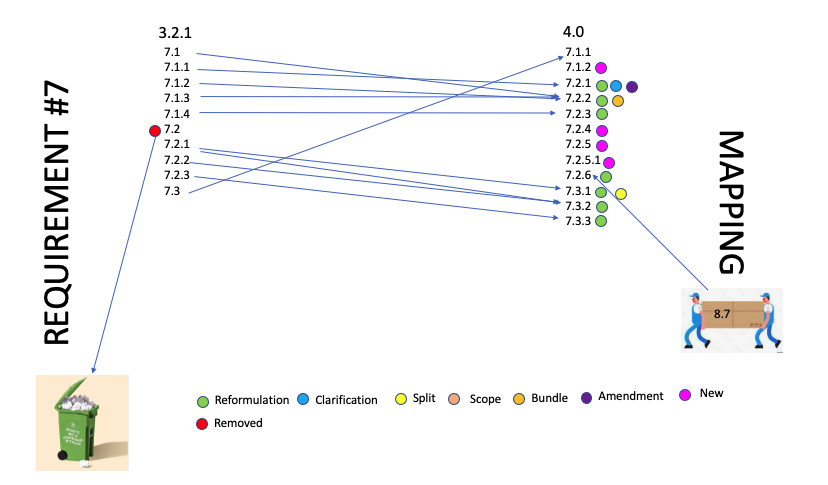
Removed: None
Moved:
- The term "Point of interaction (POI) device" is used for "devices that capture payment card data"
- The abbreviation CDE replaces " ardholder data environment"
New controls: 3 new controls
4.0 - 9.5.1.2.1 Stating that the definition of the frequency of periodic POI device inspections and the type of inspections to perform shall be determined and documented in the entity’s targeted risk analysis.
4.0 - 9.1.2 Requires Roles and responsibilities for performing activities in Requirement 9 to be documented, assigned, and understood.
4.0 - 9.2.4 requires to lock consoles ijn sensitive areas when not in use.
Changes:
- No changes
4.0 - 9.4.3 Requires to record/log the location to which media are sent out.
Removed: None
Moved:
- No move
Get your PCI 4.0 COMPLIANCE DASHBOARD TOOL . Fully aligned with PCI DSS V4.0. It includes the defined approach requirements, the customized approach, applicability notes, purpose, good practices & further information, definition, example and defined testing procedures and prioritization approach. It also provides templates to register your compensating controls, controls met with remediations but also to register your customized Controls, the outcome of the customized approach risk assessments and the risk assessments for the definition of frequency periods as well as to register execution of vulnerability scans and penetration tests.
Detailed analysis
Title:
3.2.1 - Restrict physical access to cardholder data
4.0 - Restrict Physical Access to Cardholder Data
3.2.1 - Restrict physical access to cardholder data
4.0 - Restrict Physical Access to Cardholder Data
3.2.1 - 9.1 Use appropriate facility entry controls to limit and monitor physical access to systems in the cardholder data environment.
Change: Reformulation
4.0 - 9.2.1 Appropriate facility entry controls are in place to restrict physical access to systems in the CDE.
Change: Reformulation
4.0 - 9.2.1 Appropriate facility entry controls are in place to restrict physical access to systems in the CDE.
3.2.1 - 9.1.1 Use either video cameras or access control mechanisms (or both) to monitor individual physical access to sensitive areas. Review collected data and correlate with other entries. Store for at least three months, unless otherwise restricted by law.
Change: Reformulation + Clarification
4.0 - 9.2.1.1 Individual physical access to sensitive areas within the CDE is monitored with either video cameras or physical access control mechanisms (or both) as follows:
Change: Reformulation + Clarification
4.0 - 9.2.1.1 Individual physical access to sensitive areas within the CDE is monitored with either video cameras or physical access control mechanisms (or both) as follows:
- Entry and exit points to/from sensitive areas within the CDE are monitored.
- Monitoring devices or mechanisms are protected from tampering or disabling.
- Collected data is reviewed and correlated with other entries.
- Collected data is stored for at least three months, unless otherwise restricted by law.
3.2.1 - 9.1.2 Implement physical and/or logical controls to restrict access to publicly accessible network jacks.
Change: Reformulation
4.0 - 9.2.2 Physical and/or logical controls are implemented to restrict use of publicly accessible network jacks within the facility.
Change: Reformulation
4.0 - 9.2.2 Physical and/or logical controls are implemented to restrict use of publicly accessible network jacks within the facility.
3.2.1 - 9.1.3 Restrict physical access to wireless access points, gateways, handheld devices, networking/communications hardware, and telecommunication lines.
Change: Reformulation
4.0 - 9.2.3 Physical access to wireless access points, gateways, networking/communications hardware, and telecommunication lines within the facility is restricted.
Change: Reformulation
4.0 - 9.2.3 Physical access to wireless access points, gateways, networking/communications hardware, and telecommunication lines within the facility is restricted.
3.2.1 - 9.2 Develop procedures to easily distinguish between onsite personnel and visitors, to include:
4.0 - 9.3.1 Procedures are implemented for authorizing and managing physical access of personnel to the CDE, including:
- Identifying onsite personnel and visitors (for example, assigning badges)
- Changes to access requirements
- Revoking or terminating onsite personnel and expired visitor identification (such as ID badges).
4.0 - 9.3.1 Procedures are implemented for authorizing and managing physical access of personnel to the CDE, including:
- Identifying personnel.
- Managing changes to an individual’s physical access requirements.
- Revoking or terminating personnel identification.
- Limiting access to the identification process or system to authorized personnel.
3.2.1 - 9.3 Control physical access for onsite personnel to sensitive areas as follows:
4.0 - 9.3.1.1 Physical access to sensitive areas within the CDE for personnel is controlled as follows:
- Access must be authorized and based on individual job function.
- Access is revoked immediately upon termination, and all physical access mechanisms, such as keys, access cards, etc., are returned or disabled.
4.0 - 9.3.1.1 Physical access to sensitive areas within the CDE for personnel is controlled as follows:
- Access is authorized and based on individual job function.
- Access is revoked immediately upon termination.
- All physical access mechanisms, such as keys, access cards, etc., are returned or disabled upon termination.
3.2.1- 9.4 Implement procedures to identify and authorize visitors.
Procedures should include the following:
3.2.1 - 9.4.1 Visitors are authorized before entering, and escorted at all times within, areas where cardholder data is processed or maintained.
3.2.1 - 9.4.2 Visitors are identified and given a badge or other identification that expires and that visibly distinguishes the visitors from onsite personnel.
Change: Reformulation + Merge
4.0 - 9.3.2 Procedures are implemented for authorizing and managing visitor access to the CDE, including:
Procedures should include the following:
3.2.1 - 9.4.1 Visitors are authorized before entering, and escorted at all times within, areas where cardholder data is processed or maintained.
3.2.1 - 9.4.2 Visitors are identified and given a badge or other identification that expires and that visibly distinguishes the visitors from onsite personnel.
Change: Reformulation + Merge
4.0 - 9.3.2 Procedures are implemented for authorizing and managing visitor access to the CDE, including:
- Visitors are authorized before entering.
- Visitors are escorted at all times.
- Visitors are clearly identified and given a badge or other identification that expires.
- Visitor badges or other identification visibly distinguishes visitors from personnel
3.2.1 - 9.4.3 Visitors are asked to surrender the badge or identification before leaving the facility or at the date of expiration.
Change: Reformulation + Clarification
4.0 - 9.3.3 Visitor badges or identification are surrendered or deactivated before visitors leave the facility or at the date of expiration.
Change: Reformulation + Clarification
4.0 - 9.3.3 Visitor badges or identification are surrendered or deactivated before visitors leave the facility or at the date of expiration.
3.2.1 - 9.4.4 A visitor log is used to maintain a physical audit trail of visitor activity to the facility as well as computer rooms and data centers where cardholder data is stored or transmitted.
Document the visitor’s name, the firm represented, and the onsite personnel authorizing physical access on the log.
Retain this log for a minimum of three months, unless otherwise restricted by law.
Change: Reformulation
4.0 - 9.3.4 A visitor log is used to maintain a physical record of visitor activity within the facility and within sensitive areas, including:
Document the visitor’s name, the firm represented, and the onsite personnel authorizing physical access on the log.
Retain this log for a minimum of three months, unless otherwise restricted by law.
Change: Reformulation
4.0 - 9.3.4 A visitor log is used to maintain a physical record of visitor activity within the facility and within sensitive areas, including:
- The visitor’s name and the organization represented.
- The date and time of the visit.
- The name of the personnel authorizing physical access.
- Retaining the log for at least three months, unless otherwise restricted by law.
3.2.1 - 9.5 Physically secure all media.
Change: Reformulation
4.0 - 9.4.1 All media with cardholder data is physically secured.
Change: Reformulation
4.0 - 9.4.1 All media with cardholder data is physically secured.
3.2.1 - 9.5.1 Store media backups in a secure location, preferably an off-site facility, such as an alternate or backup site, or a commercial storage facility. Review the location’s security at least annually.
Change: Reformulation + Split
4.0 - 9.4.1.1 Offline media backups with cardholder data are stored in a secure location.
4.0 - 9.4.1.2 The security of the offline media backup location(s) with cardholder data is reviewed at least once every 12 months
Change: Reformulation + Split
4.0 - 9.4.1.1 Offline media backups with cardholder data are stored in a secure location.
4.0 - 9.4.1.2 The security of the offline media backup location(s) with cardholder data is reviewed at least once every 12 months
3.2.1 - 9.6 Maintain strict control over the internal or external distribution of any kind of media, including the following:
3.2.1 - 9.6.2 Send the media by secured courier or other delivery method that can be accurately tracked.
Change: Reformulation + Merge + Clarification + Amendement
4.0 - 9.4.3 Media with cardholder data sent outside the facility is secured as follows:
3.2.1 - 9.6.2 Send the media by secured courier or other delivery method that can be accurately tracked.
Change: Reformulation + Merge + Clarification + Amendement
4.0 - 9.4.3 Media with cardholder data sent outside the facility is secured as follows:
- Media sent outside the facility is logged.
- Media is sent by secured courier or other delivery method that can be accurately tracked.
- Offsite tracking logs include details about media location.
3.2.1 - 9.6.1 Classify media so the sensitivity of the data can be determined.
Change: Reformulation
4.0- 9.4.2 All media with cardholder data is classified in accordance with the sensitivity of the data.
Change: Reformulation
4.0- 9.4.2 All media with cardholder data is classified in accordance with the sensitivity of the data.
3.2.1 - 9.6.3 Ensure management approves any and all media that is moved from a secured area (including when media is distributed to individuals).
Change: Reformulation
4.0 - 9.4.4 Management approves all media with cardholder data that is moved outside the facility (including when media is distributed to individuals).
Change: Reformulation
4.0 - 9.4.4 Management approves all media with cardholder data that is moved outside the facility (including when media is distributed to individuals).
3.2.1 - 9.7 Maintain strict control over the storage and accessibility of media.
Change: Reformulation
4.0 - 9.4.5 Inventory logs of all electronic media with cardholder data are maintained.
Change: Reformulation
4.0 - 9.4.5 Inventory logs of all electronic media with cardholder data are maintained.
3.2.1 - 9.7.1 Properly maintain inventory logs of all media and conduct media inventories at least annually.
Change: Reformulation
4.0 - 9.4.5.1 Inventories of electronic media with cardholder data are conducted at least once every 12 months.
Change: Reformulation
4.0 - 9.4.5.1 Inventories of electronic media with cardholder data are conducted at least once every 12 months.
3.2.1 - 9.8 Destroy media when it is no longer needed for business or legal reasons as follows:
3.2.1 - 9.8.1 Shred, incinerate, or pulp hard- copy materials so that cardholder data cannot be reconstructed. Secure storage containers used for materials that are to be destroyed.
Change: Reformulation + Merge
4.0 - 9.4.6 Hard-copy materials with cardholder data are destroyed when no longer needed for business or legal reasons, as follows:
3.2.1 - 9.8.1 Shred, incinerate, or pulp hard- copy materials so that cardholder data cannot be reconstructed. Secure storage containers used for materials that are to be destroyed.
Change: Reformulation + Merge
4.0 - 9.4.6 Hard-copy materials with cardholder data are destroyed when no longer needed for business or legal reasons, as follows:
- Materials are cross-cut shredded, incinerated, or pulped so that cardholder data cannot be reconstructed.
- Materials are stored in secure storage containers prior to destruction.
3.2.1 - 9.8.2 Render cardholder data on electronic media unrecoverable so that cardholder data cannot be reconstructed.
Change: Reformulation + clarification
4.0 - 9.4.7 Electronic media with cardholder data is destroyed when no longer needed for business or legal reasons via one of the following:
Change: Reformulation + clarification
4.0 - 9.4.7 Electronic media with cardholder data is destroyed when no longer needed for business or legal reasons via one of the following:
- The electronic media is destroyed.
- The cardholder data is rendered unrecoverable so that it cannot be reconstructed.
3.2.1 - 9.9 Protect devices that capture payment card data via direct physical interaction with the card from tampering and substitution.
Change: Reformulation + clarification
4.0 - 9.5.1 POI devices that capture payment card data via direct physical interaction with the payment card form factor are protected from tampering and unauthorized substitution, including the following:
Change: Reformulation + clarification
4.0 - 9.5.1 POI devices that capture payment card data via direct physical interaction with the payment card form factor are protected from tampering and unauthorized substitution, including the following:
- Maintaining a list of POI devices.
- Periodically inspecting POI devices to look for
tampering or unauthorized substitution. - Training personnel to be aware of suspicious behavior and to report tampering or unauthorized substitution of devices.
3.2.1 - 9.9.1 Maintain an up-to-date list of devices. The list should include the following:
4.0 - 9.5.1.1 An up-to-date list of POI devices is maintained, including:
- Make, model of device
- Location of device (for example, the address of the site or facility where the device is located)
- Device serial number or other method of unique identification.
4.0 - 9.5.1.1 An up-to-date list of POI devices is maintained, including:
- Make and model of the device.
- Location of device.
- Device serial number or other methods of unique identification.
3.2.1 - 9.9.2 Periodically inspect device surfaces to detect tampering (for example, addition of card skimmers to devices), or substitution (for example, by checking the serial number or other device characteristics to verify it has not been swapped with a fraudulent device).
Change: Reformulation
4.0 - 9.5.1.2 POI device surfaces are periodically inspected to detect tampering and unauthorized substitution.
Change: Reformulation
4.0 - 9.5.1.2 POI device surfaces are periodically inspected to detect tampering and unauthorized substitution.
3.2.1 - 9.9.3 Provide training for personnel to be aware of attempted tampering or replacement of devices. Training should include the following:
4.0 - 9.5.1.3 Training is provided for personnel in POI environments to be aware of attempted tampering or replacement of POI devices, and includes:
- Verify the identity of any third-party persons claiming to be repair or maintenance personnel, prior to granting them access to modify or troubleshoot devices.
- Do not install, replace, or return devices without verification.
- Be aware of suspicious behavior around devices (for example, attempts by unknown persons to unplug or open devices).
- Report suspicious behavior and indications of device tampering or substitution to appropriate personnel (for example, to a manager or security officer).
4.0 - 9.5.1.3 Training is provided for personnel in POI environments to be aware of attempted tampering or replacement of POI devices, and includes:
- Verifying the identity of any third-party persons claiming to be repair or maintenance personnel, before granting them access to modify or troubleshoot devices.
- Procedures to ensure devices are not installed, replaced, or returned without verification.
- Being aware of suspicious behavior around devices.
- Reporting suspicious behavior and indications of device tampering or substitution to appropriate personnel.
3.2.1 - 9.10 Ensure that security policies and operational procedures for restricting physical access to cardholder data are documented, in use, and known to all affected parties.
Change: Reformulation
4.0 - 9.1.1 All security policies and operational procedures that are identified in Requirement 9 are:
• Documented.
Change: Reformulation
4.0 - 9.1.1 All security policies and operational procedures that are identified in Requirement 9 are:
• Documented.
- Kept up to date.
- In use.
- Known to all affected parties.
3.2.1 - None
Change: NEW
4.0 - 9.1.2 Roles and responsibilities for performing activities in Requirement 9 are documented, assigned, and understood.
Change: NEW
4.0 - 9.1.2 Roles and responsibilities for performing activities in Requirement 9 are documented, assigned, and understood.
3.2.1 - None
Change: New
4.0 - 9.2.4 Access to consoles in sensitive areas is restricted via locking when not in use.
Change: New
4.0 - 9.2.4 Access to consoles in sensitive areas is restricted via locking when not in use.
3.2.1 - NONE
Change: NEW
4.0 - 9.5.1.2.1 The frequency of periodic POI device inspections and the type of inspections performed is defined in the entity’s targeted risk analysis, which is performed according to all elements specified in Requirement 12.3.1.
Change: NEW
4.0 - 9.5.1.2.1 The frequency of periodic POI device inspections and the type of inspections performed is defined in the entity’s targeted risk analysis, which is performed according to all elements specified in Requirement 12.3.1.
 RSS Feed
RSS Feed
