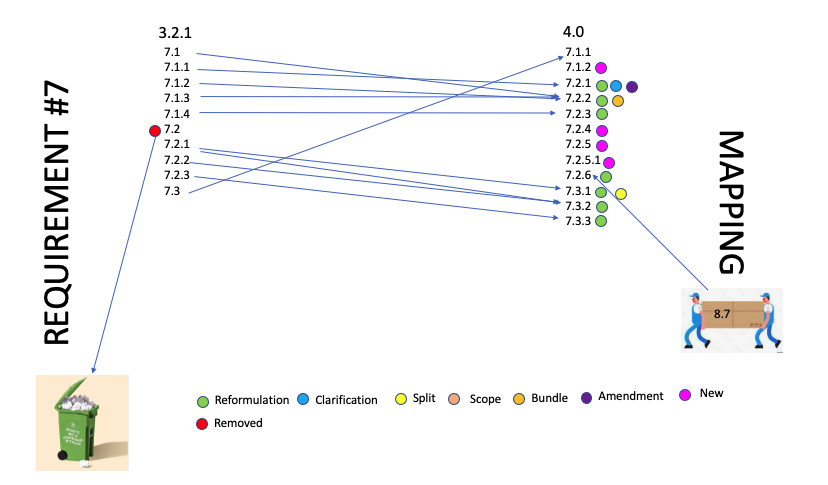
Impact of the new PCI 4.0 on the former 3.2.1 requirement 7 are in the form of : Reformulation, clarification and amendements, removal and migration.
Terminology:
New controls: 4 new controls:
4.0 - 7.1.2 requires that roles and responsibilities for performing activities in Requirement 7 are documented, assigned, and understood.
4.0 - 7.2.4 requires to periodically review appropriateness of all user access and access privileges and to handle inappropriate access as well as to seek management approval of the appropriateness of remaining access.
4.0 - 7.2.5 requires that all application and system accounts and related access privileges are assigned and managed appropriately.
4.0 - 7.2.5.1 requires to periodically review appropriateness of all application and system accounts access and access privileges and to handle inappropriate access as well as to seek management approval of the appropriateness of remaining access.
Amended:
4.0 - 7.2.1 requires, in addition to tyhe definition of access, to define an access control model.
Removed:
Requirement 3.2.1 - 7.2 has been removed for redundancy reason.
3.2.1 - 7.2 - Establish an access control system(s) for systems components that restricts access based on a user’s need to know, and is set to “deny all” unless specifically allowed.
Migrated: One control from Requirement 8 has been moved into requiremet 7
3.2.1 - 8.7 All access to any database containing cardholder data (including access by applications, administrators, and all other users) is restricted as follows:
- The term "relevant" is replaced by "applicable"
- the terms "Development environment" and "test environment" are replaced by "Pre-production environments"
- the term "custom code" is replaced by "bespoke and custom software"
New controls: 4 new controls:
4.0 - 7.1.2 requires that roles and responsibilities for performing activities in Requirement 7 are documented, assigned, and understood.
4.0 - 7.2.4 requires to periodically review appropriateness of all user access and access privileges and to handle inappropriate access as well as to seek management approval of the appropriateness of remaining access.
4.0 - 7.2.5 requires that all application and system accounts and related access privileges are assigned and managed appropriately.
4.0 - 7.2.5.1 requires to periodically review appropriateness of all application and system accounts access and access privileges and to handle inappropriate access as well as to seek management approval of the appropriateness of remaining access.
Amended:
4.0 - 7.2.1 requires, in addition to tyhe definition of access, to define an access control model.
Removed:
Requirement 3.2.1 - 7.2 has been removed for redundancy reason.
3.2.1 - 7.2 - Establish an access control system(s) for systems components that restricts access based on a user’s need to know, and is set to “deny all” unless specifically allowed.
Migrated: One control from Requirement 8 has been moved into requiremet 7
3.2.1 - 8.7 All access to any database containing cardholder data (including access by applications, administrators, and all other users) is restricted as follows:
- All user access to, user queries of, and user actions on databases are through programmatic methods.
- Only database administrators have the ability to directly access or query databases.
- Application IDs for database applications can only be used by the applications (and not by individual users or other non-application processes).
Get your PCI 4.0 COMPLIANCE DASHBOARD TOOL . Fully aligned with PCI DSS V4.0. It includes the defined approach requirements, the customized approach, applicability notes, purpose, good practices & further information, definition, example and defined testing procedures and prioritization approach. It also provides templates to register your compensating controls, controls met with remediations but also to register your customized Controls, the outcome of the customized approach risk assessments and the risk assessments for the definition of frequency periods as well as to register execution of vulnerability scans and penetration tests.
Detailed Analysis
Titre
3.2.1 - Restrict access to cardholder data by business need to know
4.0 - Restrict Access to System Components and cardholder Data by Business Need to Know
3.2.1 - Restrict access to cardholder data by business need to know
4.0 - Restrict Access to System Components and cardholder Data by Business Need to Know
3.2.1 - 7.1 Limit access to system components and cardholder data to only those individuals whose job requires such access.
Change: Split, Clarification, removal
4.0 - 7.2.2 Access is assigned to users, including privileged users, based on:
Change: Split, Clarification, removal
4.0 - 7.2.2 Access is assigned to users, including privileged users, based on:
- Job classification and function.
- Least privileges necessary to perform job responsibilities.
3.2.1 - 7.1.1 Define access needs for each role, including:
4.0 - 7.2.1 An access control model is defined and includes granting access as follows:
- System components and data resources that each role needs to access for their job function
- Level of privilege required (for example, user, administrator, etc.) for accessing resources
4.0 - 7.2.1 An access control model is defined and includes granting access as follows:
- Appropriate access depending on the entity’s business and access needs.
- Access to system components and data resources that is based on users’ job classification and functions.
- The least privileges required (for example, user, administrator) to perform a job function.
3.2.1 - 7.1.2 Restrict access to privileged user IDs to least privileges necessary to perform job responsibilities.
Change: Reformulation + Merge with 3.2.1 - 7.1.3
4.0 - 7.2.2 Access is assigned to users, including privileged users, based on:
Change: Reformulation + Merge with 3.2.1 - 7.1.3
4.0 - 7.2.2 Access is assigned to users, including privileged users, based on:
- Job classification and function.
- Least privileges necessary to perform job responsibilities.
3.2.1 - 7.1.3 Assign access based on individual personnel’s job classification and function.
Change: Reformulation + Merge with 3.2.1 -7.1.2
4.0 - 7.2.2 Access is assigned to users, including privileged users, based on:
Change: Reformulation + Merge with 3.2.1 -7.1.2
4.0 - 7.2.2 Access is assigned to users, including privileged users, based on:
- Job classification and function.
- Least privileges necessary to perform job responsibilities.
3.2.1 - 7.1.4 Require documented approval by authorized parties specifying required privileges.
Change: Reformulation
4.0 - 7.2.3 Required privileges are approved by authorized personnel.
Change: Reformulation
4.0 - 7.2.3 Required privileges are approved by authorized personnel.
3.2.1 - 7.2 Establish an access control system(s) for systems components that restricts access based on a user’s need to know, and is set to “deny all” unless specifically allowed.
Change: Removed
Change: Removed
3.2.1 - 7.2.1 This access control system(s) must include the following: Coverage of all system components
Change: Split + Reformulation
4.0 - 7.3.1 An access control system(s) is in place that restricts access based on a user’s need to know and covers all system components.
4.0 - 7.3.2 This access control system(s) must include the following: The access control system(s) is configured to enforce permissions assigned to individuals, applications, and systems based on job classification and function.
Change: Split + Reformulation
4.0 - 7.3.1 An access control system(s) is in place that restricts access based on a user’s need to know and covers all system components.
4.0 - 7.3.2 This access control system(s) must include the following: The access control system(s) is configured to enforce permissions assigned to individuals, applications, and systems based on job classification and function.
3.2.1 - 7.2.2 Assignment of privileges to individuals based on job classification and function.
Change: Reformulation
4.0 - 7.3.2 The access control system(s) is configured to enforce permissions assigned to individuals, applications, and systems based on job classification and function.
Change: Reformulation
4.0 - 7.3.2 The access control system(s) is configured to enforce permissions assigned to individuals, applications, and systems based on job classification and function.
4.0 - 7.2.3 This access control system(s) must include the following: Default “deny-all” setting.
Change: Reformulation
4.0 - 7.3.3 The access control system(s) is set to “deny all” by default.
Change: Reformulation
4.0 - 7.3.3 The access control system(s) is set to “deny all” by default.
3.2.1 - 7.3 Ensure that security policies and operational procedures for restricting access to cardholder data are documented, in use, and known to all affected parties.
Change: Reformulation
4.0 - 7.1.1 All security policies and operational procedures that are identified in Requirement 7 are:
• Documented.
Change: Reformulation
4.0 - 7.1.1 All security policies and operational procedures that are identified in Requirement 7 are:
• Documented.
- Kept up to date.
- In use.
- Known to all affected parties.
3.2.1 - None
Change: NEW
4.0 - 7.2.5 All application and system accounts and related access privileges are assigned and managed as follows:
Change: NEW
4.0 - 7.2.5 All application and system accounts and related access privileges are assigned and managed as follows:
- Based on the least privileges necessary for the operability of the system or application.
- Access is limited to the systems, applications, or processes that specifically require their use.
3.2.1 - None
Change: NEW.
4.0 - 7.2.5.1 All access by application and system accounts and related access privileges are reviewed as follows:
Change: NEW.
4.0 - 7.2.5.1 All access by application and system accounts and related access privileges are reviewed as follows:
- Periodically (at the frequency defined in the entity’s targeted risk analysis, which is performed according to all elements specified in Requirement 12.3.1).
- The application/system access remains appropriate for the function being performed.
- Any inappropriate access is addressed.
- Management acknowledges that access remains
appropriate.
3.2.1 - 8.7 All access to any database containing cardholder data (including access by applications, administrators, and all other users) is restricted as follows:
4.0 - 7.2.6 All user access to query repositories of stored cardholder data is restricted as follows:
- All user access to, user queries of, and user actions on databases are through programmatic methods.
- Only database administrators have the ability to directly access or query databases.
- Application IDs for database applications can only be used by the applications (and not by individual users or other non-application processes).
4.0 - 7.2.6 All user access to query repositories of stored cardholder data is restricted as follows:
- Via applications or other programmatic methods, with access and allowed actions based on user roles and least privileges.
- Only the responsible administrator(s) can directly access or query repositories of stored CHD.
 RSS Feed
RSS Feed
