Overview
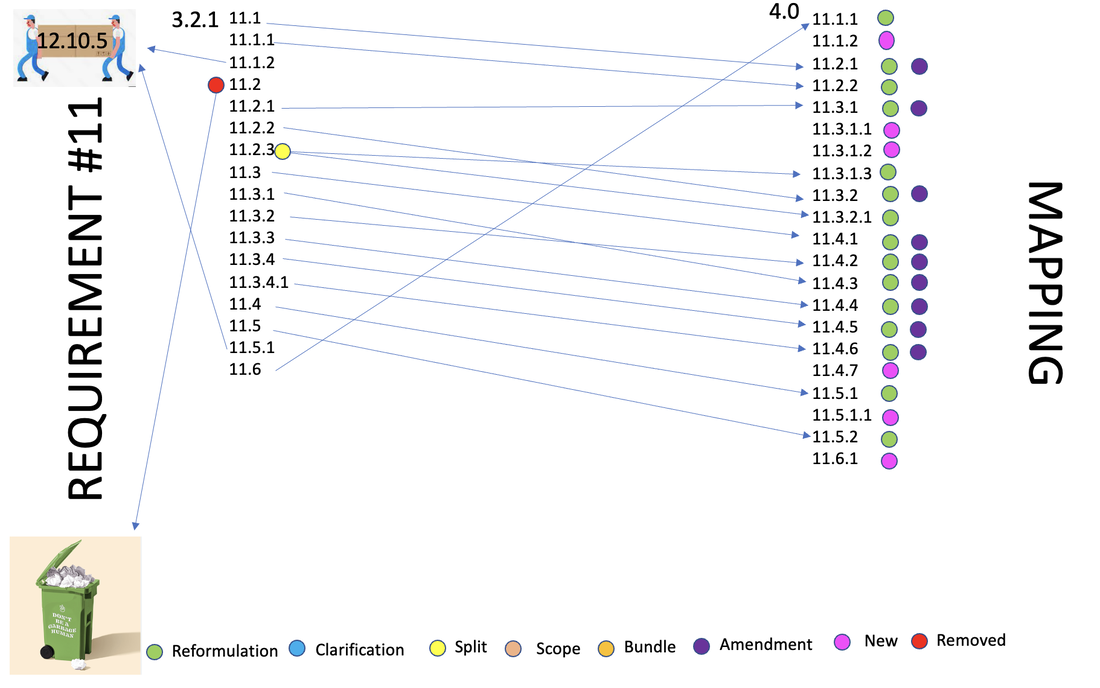
The impact of the new PCI 4.0 on the former 3.2.1 requirement 11 is in the form of: Reformulation, amendments, split, move and removal.
Terminology:
4.0 - 11.1.2 requests that roles and responsibilities for performing activities in Requirement 11 be documented, assigned, and understood.
4.0 - 11.3.1.1 requests that vulnerabilities not ranked as high-risk or critical be addressed based on the risk defined in the entity’s targeted risk analysis.
4.0 - 11.3.1.2 requests to perform internal vulnerability scans via authenticated scanning and clarify how it should be done.
4.0 - 11.4.7 requests that service providers support their customers for external penetration testing (**)
4.0 - 11.5.1.1 request that service providers implement Intrusion-detection and/or intrusion-prevention techniques to detect, alert on/prevent, and address covert malware communication channels (**)
4.0 - 11.6.1 requests that unauthorized changes of headers and the contents of payment pages be detected and responded to.
(*) Organizations should integrate PCI-DSS requirements in terms of penetration testing in the selection process of service providers to avoid any bad surprise.
(**) The challenge here is that by definition Covert Channels are intended to be hidden. This point should be clarified by the Council.
Amended:
4.0 - 11.2.1 requests that whenever automated monitoring is used to detect wireless access point, personnel must be notified via generated alerts(*).
4.0 - 11.4.1 requests that the approach to assessing and addressing the risk posed by exploitable vulnerabilities and security weaknesses found during a penetration testing be documented in the methodology.
4.0 - 11.4.4 request that penetration testing exploitable findings be corrected in accordance with the entity’s assessment of the risk posed by the security issue.
4.0 - 11.3.1 requests Internal vulnerability Scan tool be kept up to date with latest vulnerability information and organizational independence of the testers.
4.0 - 11.3.2 requests that ASV Program Guide requirements for a passing external vulnerability scans are met.
4.0 - 11.4.2 requests internal penetration testing be performed per the entity’s defined methodology, by a qualified internal resource or qualified external third-party and that organizational independence of the tester exists.
4.0 - 11.4.3 requests external penetration testing be performed per the entity’s defined methodology, by a qualified internal resource or qualified external third-party and that organizational independence of the tester exists.
4.0 - 11.4.5 11.4.6 request penetration tests on segmentation controls to cover all segmentation controls/methods in use, be performed according to the entity’s defined penetration testing methodology, confirm effectiveness of any use of isolation to separate systems with differing security levels, be performed by a qualified internal resource or qualified external third party.
(*) The challenge with authenticated scanning is the volume of findings these scans typically return, often numbering in the thousands.
Removed: The following controls are removed for clarity and structure
3.2.1 - 11.2 Run internal and external network vulnerability scans at least quarterly and after any significant change in the network (such as new system component installations, changes in network topology, firewall rule modifications, product upgrades).
Moved:
3.2.1 - 11.1.2 requiring incident response procedures to handle detection of unauthorized wireless access points is moved under 12.10.5
3.2.1 - 11.5.1 requiring a process to respond to alerts generated by the change-detection solution is also moved under 12.10.5
- The term quarterly is replaced by "every three months"
4.0 - 11.1.2 requests that roles and responsibilities for performing activities in Requirement 11 be documented, assigned, and understood.
4.0 - 11.3.1.1 requests that vulnerabilities not ranked as high-risk or critical be addressed based on the risk defined in the entity’s targeted risk analysis.
4.0 - 11.3.1.2 requests to perform internal vulnerability scans via authenticated scanning and clarify how it should be done.
4.0 - 11.4.7 requests that service providers support their customers for external penetration testing (**)
4.0 - 11.5.1.1 request that service providers implement Intrusion-detection and/or intrusion-prevention techniques to detect, alert on/prevent, and address covert malware communication channels (**)
4.0 - 11.6.1 requests that unauthorized changes of headers and the contents of payment pages be detected and responded to.
(*) Organizations should integrate PCI-DSS requirements in terms of penetration testing in the selection process of service providers to avoid any bad surprise.
(**) The challenge here is that by definition Covert Channels are intended to be hidden. This point should be clarified by the Council.
Amended:
4.0 - 11.2.1 requests that whenever automated monitoring is used to detect wireless access point, personnel must be notified via generated alerts(*).
4.0 - 11.4.1 requests that the approach to assessing and addressing the risk posed by exploitable vulnerabilities and security weaknesses found during a penetration testing be documented in the methodology.
4.0 - 11.4.4 request that penetration testing exploitable findings be corrected in accordance with the entity’s assessment of the risk posed by the security issue.
4.0 - 11.3.1 requests Internal vulnerability Scan tool be kept up to date with latest vulnerability information and organizational independence of the testers.
4.0 - 11.3.2 requests that ASV Program Guide requirements for a passing external vulnerability scans are met.
4.0 - 11.4.2 requests internal penetration testing be performed per the entity’s defined methodology, by a qualified internal resource or qualified external third-party and that organizational independence of the tester exists.
4.0 - 11.4.3 requests external penetration testing be performed per the entity’s defined methodology, by a qualified internal resource or qualified external third-party and that organizational independence of the tester exists.
4.0 - 11.4.5 11.4.6 request penetration tests on segmentation controls to cover all segmentation controls/methods in use, be performed according to the entity’s defined penetration testing methodology, confirm effectiveness of any use of isolation to separate systems with differing security levels, be performed by a qualified internal resource or qualified external third party.
(*) The challenge with authenticated scanning is the volume of findings these scans typically return, often numbering in the thousands.
Removed: The following controls are removed for clarity and structure
3.2.1 - 11.2 Run internal and external network vulnerability scans at least quarterly and after any significant change in the network (such as new system component installations, changes in network topology, firewall rule modifications, product upgrades).
Moved:
3.2.1 - 11.1.2 requiring incident response procedures to handle detection of unauthorized wireless access points is moved under 12.10.5
3.2.1 - 11.5.1 requiring a process to respond to alerts generated by the change-detection solution is also moved under 12.10.5
Get your PCI 4.0 COMPLIANCE DASHBOARD TOOL . Fully aligned with PCI DSS V4.0. It includes the defined approach requirements, the customized approach, applicability notes, purpose, good practices & further information, definition, example and defined testing procedures and prioritization approach. It also provides templates to register your compensating controls, controls met with remediations but also to register your customized Controls, the outcome of the customized approach risk assessments and the risk assessments for the definition of frequency periods as well as to register execution of vulnerability scans and penetration tests
Detailed Analysis
Title:
3.2.1 - Regularly test security systems and processes.
4.0 - Test Security of Systems and Networks Regularly
3.2.1 - Regularly test security systems and processes.
4.0 - Test Security of Systems and Networks Regularly
3.2.1 - 11.1 Implement processes to test for the presence of wireless access points (802.11), and detect and identify all authorized and unauthorized wireless access points on a quarterly basis.
Change: Reformulation + Amendement
4.0 - 11.2.1 Authorized and unauthorized wireless access points are managed as follows:
Change: Reformulation + Amendement
4.0 - 11.2.1 Authorized and unauthorized wireless access points are managed as follows:
- The presence of wireless (Wi-Fi) access points is tested for,
- All authorized and unauthorized wireless access points are detected and identified,
- Testing, detection, and identification occurs at least once every three months.
- If automated monitoring is used, personnel are notified via generated alerts.
3.2.1 - 11.1.1 Maintain an inventory of authorized wireless access points including a documented business justification.
Change: Reformulation
4.0 - 11.2.2 An inventory of authorized wireless access points is maintained, including a documented business justification.
Change: Reformulation
4.0 - 11.2.2 An inventory of authorized wireless access points is maintained, including a documented business justification.
3.2.1 - 11.1.2 Implement incident response procedures in the event unauthorized wireless access points are detected.
Change: MOVED to Requirement 12
4.0 - 12.10.5 The security incident response plan includes monitoring and responding to alerts from security monitoring systems, including but not limited to:
Change: MOVED to Requirement 12
4.0 - 12.10.5 The security incident response plan includes monitoring and responding to alerts from security monitoring systems, including but not limited to:
- Intrusion-detection and intrusion-prevention systems.
- Network security controls.
- Change-detection mechanisms for critical files.
- The change-and tamper-detection mechanism for payment pages.
- Detection of unauthorized wireless access points.
3.2.1 - 11.2 Run internal and external network vulnerability scans at least quarterly and after any significant change in the network (such as new system component installations, changes in network topology, firewall rule modifications, product upgrades).
Change: Removed
4.0 - NONE
Change: Removed
4.0 - NONE
3.2.1 - 11.2.1 Perform quarterly internal vulnerability scans. Address vulnerabilities and perform rescans to verify all “high risk” vulnerabilities are resolved in accordance with the entity’s vulnerability ranking (per Requirement 6.1). Scans must be performed by qualified personnel.
Change: Reformulation + Amendments
4.0 - 11.3.1 Internal vulnerability scans are performed as follows:
Change: Reformulation + Amendments
4.0 - 11.3.1 Internal vulnerability scans are performed as follows:
- At least once every three months.
- High-risk and critical vulnerabilities (per the entity’s vulnerability risk rankings defined at Requirement 6.3.1) are resolved.
- Rescans are performed that confirm all high- risk and critical vulnerabilities (as noted above) have been resolved.
- Scan tool is kept up to date with latest vulnerability information.
- Scans are performed by qualified personnel and organizational independence of the tester exists.
3.2.1 - 11.2.2 Perform quarterly external vulnerability scans, via an Approved Scanning Vendor (ASV) approved by the Payment Card Industry Security Standards Council (PCI SSC). Perform rescans as needed, until passing scans are achieved.
Change: Reformulation + Amendments
4.0 - 11.3.2 External vulnerability scans are performed as follows:
Change: Reformulation + Amendments
4.0 - 11.3.2 External vulnerability scans are performed as follows:
- At least once every three months.
- By a PCI SSC Approved Scanning Vendor (ASV).
- Vulnerabilities are resolved and ASV Program Guide requirements for a passing scan are met.
- Rescans are performed as needed to confirm that vulnerabilities are resolved per the ASV Program Guide requirements for a passing scan.
3.2.1 - 11.2.3 Perform internal and external scans, and rescans as needed, after any significant change. Scans must be performed by qualified personnel.
Change: Reformulation + split
4.0 - 11.3.1.3 Internal vulnerability scans are performed after any significant change as follows:
Change: Reformulation + split
4.0 - 11.3.1.3 Internal vulnerability scans are performed after any significant change as follows:
- High-risk and critical vulnerabilities (per the entity’s vulnerability risk rankings defined at Requirement 6.3.1) are resolved.
- Rescans are conducted as needed.
- Scans are performed by qualified personnel and organizational independence of the tester exists (not required to be a QSA or ASV).
- Vulnerabilities that are scored 4.0 or higher by the CVSS are resolved.
- Rescans are conducted as needed.
- Scans are performed by qualified personnel and organizational independence of the tester exists (not required to be a QSA or ASV).
3.2.1 - 11.3 Implement a methodology for penetration testing that includes the following:
4.0 - 11.4.1 A penetration testing methodology is defined, documented, and implemented by the entity, and includes:
- Is based on industry-accepted penetration testing approaches (for example, NIST SP800-115)
- Includes coverage for the entire CDE perimeter and critical systems
- Includes testing from both inside and outside the network
- Includes testing to validate any segmentation and scope-reduction controls
- Defines application-layer penetration tests to include, at a minimum, the vulnerabilities listed in Requirement 6.5
- Defines network-layer penetration tests to include components that support network functions as well as operating systems
- Includes review and consideration of threats and vulnerabilities experienced in the last 12 months
- Specifies retention of penetration testing results and remediation activities results.
4.0 - 11.4.1 A penetration testing methodology is defined, documented, and implemented by the entity, and includes:
- Industry-accepted penetration testing approaches.
- Coverage for the entire CDE perimeter and critical systems.
- Testing from both inside and outside the network.
- Testing to validate any segmentation and scope- reduction controls.
- Application-layer penetration testing to identify, at a minimum, the vulnerabilities listed in Requirement 6.2.4.
- Network-layer penetration tests that encompass all components that support network functions as well as operating systems.
- Review and consideration of threats and vulnerabilities experienced in the last 12 months.
- Documented approach to assessing and addressing the risk posed by exploitable vulnerabilities and security weaknesses found during penetration testing.
- Retention of penetration testing results and remediation activities results for at least 12 months.
3.2.1 - 11.3.1 Perform external penetration testing at least annually and after any significant infrastructure or application upgrade or modification (such as an operating system upgrade, a sub-network added to the environment, or a web server added to the environment).
Change: Reformulation + amendments
4.0 - 11.4.3 External penetration testing is performed:
Change: Reformulation + amendments
4.0 - 11.4.3 External penetration testing is performed:
- Per the entity’s defined methodology
- At least once every 12 months
- After any significant infrastructure or application upgrade or change
- By a qualified internal resource or qualified external third party
- Organizational independence of the tester exists (not required to be a QSA or ASV).
3.2.1 - 11.3.2 Perform internal penetration testing at least annually and after any significant infrastructure or application upgrade or modification (such as an operating system upgrade, a sub-network added to the environment, or a web server added to the environment).
Change: Reformulation + amendments
4.0 - 11.4.2 Internal penetration testing is performed:
Change: Reformulation + amendments
4.0 - 11.4.2 Internal penetration testing is performed:
- Per the entity’s defined methodology,
- At least once every 12 months
- After any significant infrastructure or application upgrade or change
- By a qualified internal resource or qualified external third-party
- Organizational independence of the tester exists (not required to be a QSA or ASV).
3.2.1 - 11.3.3 Exploitable vulnerabilities found during penetration testing are corrected and testing is repeated to verify the corrections.
Change: Reformulation + Amendement
4.0 - 11.4.4 Exploitable vulnerabilities and security weaknesses found during penetration testing are corrected as follows:
Change: Reformulation + Amendement
4.0 - 11.4.4 Exploitable vulnerabilities and security weaknesses found during penetration testing are corrected as follows:
- In accordance with the entity’s assessment of the risk posed by the security issue as defined in Requirement 6.3.1.
- Penetration testing is repeated to verify the corrections.
3.2.1 - 11.3.4 If segmentation is used to isolate the CDE from other networks, perform penetration tests at least annually and after any changes to segmentation controls/methods to verify that the segmentation methods are operational and effective, and isolate all out-of-scope systems from systems in the CDE.
Change: Reformulation + amendments
4.0 - 11.4.5 If segmentation is used to isolate the CDE from other networks, penetration tests are performed on segmentation controls as follows:
Change: Reformulation + amendments
4.0 - 11.4.5 If segmentation is used to isolate the CDE from other networks, penetration tests are performed on segmentation controls as follows:
- At least once every 12 months and after any changes to segmentation controls/methods
- Covering all segmentation controls/methods in use.
- According to the entity’s defined penetration testing methodology.
- Confirming that the segmentation controls/methods are operational and effective, and isolate the CDE from all out-of-scope systems.
- Confirming effectiveness of any use of isolation to separate systems with differing security levels (see Requirement 2.2.3).
- Performed by a qualified internal resource or qualified external third party.
- Organizational independence of the tester exists (not required to be a QSA or ASV).
3.2.1 - 11.3.4.1 Additional requirement for service providers only: If segmentation is used, confirm PCI DSS scope by performing penetration testing on segmentation controls at least every six months and after any changes to segmentation controls/methods.
Change: Reformulation + amendments
4.0 - 11.4.6 Additional requirement for service providers only: If segmentation is used to isolate the CDE from other networks, penetration tests are performed on segmentation controls as follows:
Change: Reformulation + amendments
4.0 - 11.4.6 Additional requirement for service providers only: If segmentation is used to isolate the CDE from other networks, penetration tests are performed on segmentation controls as follows:
- At least once every six months and after any changes to segmentation controls/methods.
- Covering all segmentation controls/methods in use.
- According to the entity’s defined penetration testing methodology.
- Confirming that the segmentation controls/methods are operational and effective, and isolate the CDE from all out-of-scope systems.
- Confirming effectiveness of any use of isolation to separate systems with differing security levels (see Requirement 2.2.3).
- Performed by a qualified internal resource or qualified external third party.
- Organizational independence of the tester exists (not required to be a QSA or ASV).
3.2.1 - 11.4 Use intrusion-detection and/or intrusion-prevention techniques to detect and/or prevent intrusions into the network. Monitor all traffic at the perimeter of the cardholder data environment as well as at critical points in the cardholder data environment, and alert personnel to suspected compromises.
Keep all intrusion-detection and prevention engines, baselines, and signatures up to date.
Change: Reformulation
4.0 - 11.5.1 Intrusion-detection and/or intrusion- prevention techniques are used to detect and/or prevent intrusions into the network as follows:
Keep all intrusion-detection and prevention engines, baselines, and signatures up to date.
Change: Reformulation
4.0 - 11.5.1 Intrusion-detection and/or intrusion- prevention techniques are used to detect and/or prevent intrusions into the network as follows:
- All traffic is monitored at the perimeter of the CDE.
- All traffic is monitored at critical points in the CDE.
- Personnel are alerted to suspected compromises.
- All intrusion-detection and prevention engines, baselines, and signatures are kept up to date.
3.2.1 - 11.5 Deploy a change-detection mechanism (for example, file-integrity monitoring tools) to alert personnel to unauthorized modification (including changes, additions, and deletions) of critical system files, configuration files, or content files; and configure the software to perform critical file comparisons at least weekly.
Change: Reformulation
4.0 - 11.5.2 A change-detection mechanism (for example, file integrity monitoring tools) is deployed as follows:
Change: Reformulation
4.0 - 11.5.2 A change-detection mechanism (for example, file integrity monitoring tools) is deployed as follows:
- To alert personnel to unauthorized modification (including changes, additions, and deletions) of critical files.
- To perform critical file comparisons at least once weekly.
3.2.1 - 11.5.1 Implement a process to respond to any alerts generated by the change- detection solution.
Change: Moved under 12.10.5
4.0 - 12.10.5 The security incident response plan includes monitoring and responding to alerts from security monitoring systems, including but not limited to:
Change: Moved under 12.10.5
4.0 - 12.10.5 The security incident response plan includes monitoring and responding to alerts from security monitoring systems, including but not limited to:
- Intrusion-detection and intrusion-prevention systems.
- Network security controls.
- Change-detection mechanisms for critical files.
- The change-and tamper-detection mechanism for payment pages.
- Detection of unauthorized wireless access points.
3.2.1 - 11.6 Ensure that security policies and operational procedures for security monitoring and testing are documented, in use, and known to all affected parties.
Change: Reformulation
4.0 - 11.1.1 All security policies and operational procedures that are identified in Requirement 11 are:
• Documented.
Change: Reformulation
4.0 - 11.1.1 All security policies and operational procedures that are identified in Requirement 11 are:
• Documented.
- Kept up to date.
- In use.
- Known to all affected parties.
3.2.1 - None
Change : NEW
4.0 - 11.1.2 Roles and responsibilities for performing activities in Requirement 11 are documented, assigned, and understood.
Change : NEW
4.0 - 11.1.2 Roles and responsibilities for performing activities in Requirement 11 are documented, assigned, and understood.
3.2.1 - None
Change : NEW
4.0 - 11.3.1.1 All other applicable vulnerabilities (those not ranked as high-risk or critical per the entity’s vulnerability risk rankings defined at Requirement 6.3.1) are managed as follows:
Change : NEW
4.0 - 11.3.1.1 All other applicable vulnerabilities (those not ranked as high-risk or critical per the entity’s vulnerability risk rankings defined at Requirement 6.3.1) are managed as follows:
- Addressed based on the risk defined in the entity’s targeted risk analysis, which is performed according to all elements specified in Requirement 12.3.1.
- Rescans are conducted as needed.
3.2.1 - None
Change : NEW
4.0 - 11.3.1.2 Internal vulnerability scans are performed via authenticated scanning as follows:
Change : NEW
4.0 - 11.3.1.2 Internal vulnerability scans are performed via authenticated scanning as follows:
- Systems that are unable to accept credentials for authenticated scanning are documented.
- Sufficient privileges are used for those systems that accept credentials for scanning.
- If accounts used for authenticated scanning can be used for interactive login, they are managed in accordance with Requirement 8.2.2.
3.2.1 - None
Change : NEW
11.4.7 Additional requirement for multi-tenant service providers only: Multi-tenant service providers support their customers for external penetration testing per Requirement 11.4.3 and 11.4.4.
Change : NEW
11.4.7 Additional requirement for multi-tenant service providers only: Multi-tenant service providers support their customers for external penetration testing per Requirement 11.4.3 and 11.4.4.
3.2.1 - None
Change : NEW
11.5.1.1 Additional requirement for service providers only: Intrusion-detection and/or intrusion-prevention techniques detect, alert on/prevent, and address covert malware communication channels.
Change : NEW
11.5.1.1 Additional requirement for service providers only: Intrusion-detection and/or intrusion-prevention techniques detect, alert on/prevent, and address covert malware communication channels.
3.2.1 - None
Change : NEW
11.6.1 A change- and tamper-detection mechanism is deployed as follows:
Change : NEW
11.6.1 A change- and tamper-detection mechanism is deployed as follows:
- To alert personnel to unauthorized modification (including indicators of compromise, changes, additions, and deletions) to the HTTP headers and the contents of payment pages as received by the consumer browser.
- The mechanism is configured to evaluate the received HTTP header and payment page.
- The mechanism functions are performed as follows:
- – At least once every seven days
OR - – Periodically (at the frequency defined in the entity’s targeted risk analysis, which is performed according to all elements specified in Requirement 12.3.1).
- – At least once every seven days
 RSS Feed
RSS Feed
