Overview
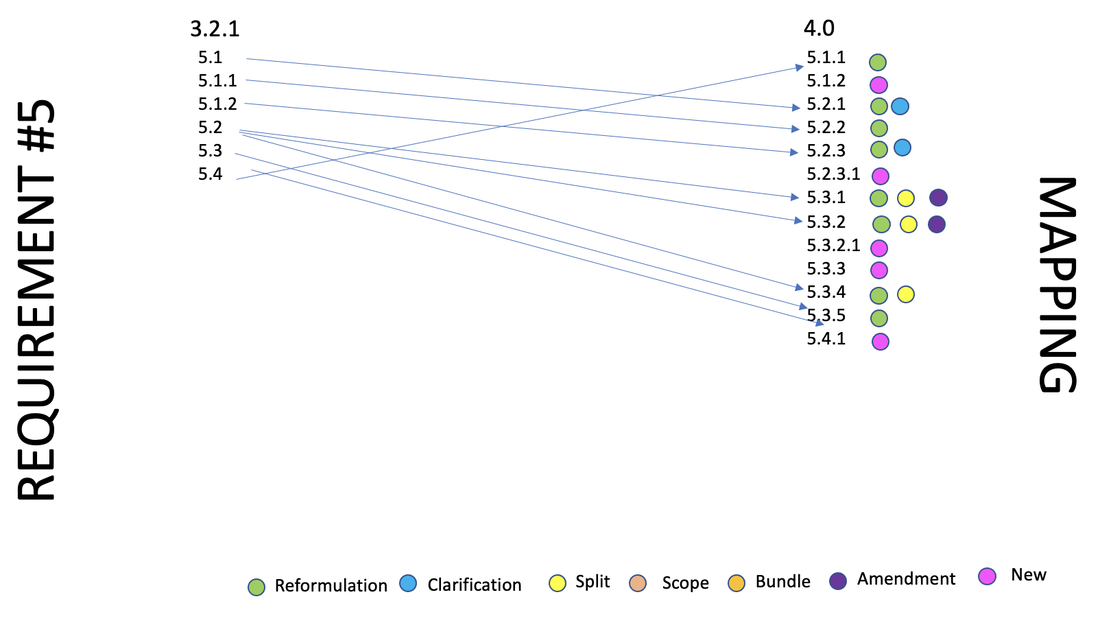
Impact of the new PCI 4.0 on the former 3.2.1 requirement 5 are in the form of : Reformulation, clarification and amendements. This version of requirement 5 contains quite more controls than in 3.2.1, mainly through new additions or the split of one control. It also introduces new concepts (for PCI) such as behavioral analysis, real-time scan and phishing attacks. Two controls are subjected to targeted risk analysis.
Terminology:
New controls: 5 new controls:
Split:
3.2.1 - 5.2 is split into 4.0 - 5.3.1 , 5.3.2 and 5.3.4.
Amendments:
4.0 - 5.3.1 Require that anti-malware be updated automatically.
4.0 - 5.3.2 Introduce the notion of continuous behavioral analysis of systems or processes.
4.0 - 5.3.2 In addition to periodic scanning, "real-time scanning" (on-access) scans shall also be performed every time an object is downloaded, open, modified. Those running traditional anti-malware tools, will need to do both periodic and real-time scanning which could introduce additional load to systems in scope. Most modern anti-malware platforms already include both.
Moved: None
Removed: None
- The terms virus and "anti-virus" are respectively replaced by "malicious software" and by "anti-malware". This to onboard malware variants such as worms, trojans, ransomware, spyware, rootkits, adware, backdoors, etc.
- The mention "Actively running" is replaced by "Real-time scanning". This to avoid past misunderstandings. Real-time scanning should be understood as a type of persistent, on-access scanning.
- "Behavioral analysis" is incorporated as an accepted anti-malware solution scanning method, as an alternative to traditional periodic (scheduled and on-demand) and real-time (on-access) scans. Behavior-based malware detection evaluates an object based on its intended actions before it can actually execute that behavior. An object’s behavior, or in some cases its potential behavior, is analyzed for suspicious activities. Attempts to perform actions that are clearly abnormal or unauthorized would indicate the object is malicious, or at least suspicious.”
New controls: 5 new controls:
- 4.0 - 5.1.2 Generic statement about roles and responsibilities
- 4.0 - 5.2.3.1 Organizations should perform a periodic assessment to determine which system components should require an anti-malware solution. Assets that are determined not to be affected by malware should be included in a list. The frequency of periodic evaluations of system components not at risk for malware shall be the result of a targeted risk analysis.
- 4.0 5.3.2.1 The frequency of periodic malware scans shall be the outcome of a target risk analysis.
- 4.0 - 5.3.3 Removable electronic media must be automatically scanned when the media is inserted, connected, or logically mounted. The wording of the requirement, the testing procedures, and the guidance all indicate a requirement to scan the entire media/device upon connection, and not merely scan files on access.
- 4.0-5.4.1Mandatory detection and protection against phishing attacks. By adding this requirement, the PCI Security Standards Council has acknowledged that email is a major attack vector and the most successful attack is phishing.
Split:
3.2.1 - 5.2 is split into 4.0 - 5.3.1 , 5.3.2 and 5.3.4.
Amendments:
4.0 - 5.3.1 Require that anti-malware be updated automatically.
4.0 - 5.3.2 Introduce the notion of continuous behavioral analysis of systems or processes.
4.0 - 5.3.2 In addition to periodic scanning, "real-time scanning" (on-access) scans shall also be performed every time an object is downloaded, open, modified. Those running traditional anti-malware tools, will need to do both periodic and real-time scanning which could introduce additional load to systems in scope. Most modern anti-malware platforms already include both.
Moved: None
Removed: None
PCI 4.0 Compliance Dashboard
Get your PCI 4.0 COMPLIANCE DASHBOARD TOOL . Fully aligned with PCI DSS V4.0. It includes the defined approach requirements, the customized approach, applicability notes, purpose, good practices & further information, definition, example and defined testing procedures and prioritization approach. It also provides templates to register your compensating controls, controls met with remediations but also to register your customized Controls, the outcome of the customized approach risk assessments and the risk assessments for the definition of frequency periods as well as to register execution of vulnerability scans and penetration tests.
Get your PCI 4.0 COMPLIANCE DASHBOARD TOOL . Fully aligned with PCI DSS V4.0. It includes the defined approach requirements, the customized approach, applicability notes, purpose, good practices & further information, definition, example and defined testing procedures and prioritization approach. It also provides templates to register your compensating controls, controls met with remediations but also to register your customized Controls, the outcome of the customized approach risk assessments and the risk assessments for the definition of frequency periods as well as to register execution of vulnerability scans and penetration tests.
Detailed Analysis
Titre
3.2.1 - Protect all systems against malware and regularly update anti-virus software or programs
4.0 - Protect all Systems and networks from malicious software
3.2.1 - Protect all systems against malware and regularly update anti-virus software or programs
4.0 - Protect all Systems and networks from malicious software
3.2.1 - 5.1 Deploy anti-virus software on all systems commonly affected by malicious software (particularly personal computers and servers).
Change: Reformulation + Clarification.
4.0 - 5.2.1An anti-malware solution(s) is deployed on all system components, except for those system components identified in periodic evaluations per Requirement 5.2.3 that concludes the system components are not at risk from malware.
Change: Reformulation + Clarification.
4.0 - 5.2.1An anti-malware solution(s) is deployed on all system components, except for those system components identified in periodic evaluations per Requirement 5.2.3 that concludes the system components are not at risk from malware.
3.2.1 - 5.1.1 Ensure that anti-virus programs are capable of detecting, removing, and protecting against all known types of malicious software.
Change: Reformulation.
4.0 - 5.2.2 The deployed anti-malware solution(s):
Change: Reformulation.
4.0 - 5.2.2 The deployed anti-malware solution(s):
- Detects all known types of malware.
- Removes, blocks, or contains all known types of malware.
3.2.1 - 5.1.2For systems considered to be not commonly affected by malicious software, perform periodic evaluations to identify and evaluate evolving malware threats in order to confirm whether such systems continue to not require anti-virus software.
Change: Reformulation + Clarification
4.0 - 5.2.3Any system components that are not at risk for malware are evaluated periodically to include the following:
Notes:
Organizations must perform a Targeted Risk Analysis (TRA) with the goal of establishing a frequency to review systems not at risk for malware. This review is an evaluation to determine if the threat landscape has changed and therefore may require additional controls outside of traditional anti-malware installations. There are several components which typically do not have or cannot have anti-malware agents installed such as Mainframes, Vendor Appliances, or low-level operating systems such as ESXi (VMware), Kubernetes Clusters, etc. QSAs will be looking for organizations to establish a reasonable frequency based on the TRA and demonstrate the timeframe has been followed. c
Using industry and vendor sources to identify emerging malware and attacks on systems.
Change: Reformulation + Clarification
4.0 - 5.2.3Any system components that are not at risk for malware are evaluated periodically to include the following:
- A documented list of all system components not at risk for malware.
- Identification and evaluation of evolving malware threats for those system components.
- Confirmation whether such system components continue to not require anti-malware protection.
Notes:
Organizations must perform a Targeted Risk Analysis (TRA) with the goal of establishing a frequency to review systems not at risk for malware. This review is an evaluation to determine if the threat landscape has changed and therefore may require additional controls outside of traditional anti-malware installations. There are several components which typically do not have or cannot have anti-malware agents installed such as Mainframes, Vendor Appliances, or low-level operating systems such as ESXi (VMware), Kubernetes Clusters, etc. QSAs will be looking for organizations to establish a reasonable frequency based on the TRA and demonstrate the timeframe has been followed. c
Using industry and vendor sources to identify emerging malware and attacks on systems.
3.2.1 - 5.2Ensure that all anti-virus mechanisms are maintained as follows:
Change: Reformulation + Split + amendment
4.0 - 5.3.1The anti-malware solution(s) is kept current via automatic updates.
4.0 - 5.3.2The anti-malware solution(s):
- Are kept current,
- Perform periodic scans
- Generate audit logs which are retained per PCI DSS Requirement 10.7.
Change: Reformulation + Split + amendment
4.0 - 5.3.1The anti-malware solution(s) is kept current via automatic updates.
4.0 - 5.3.2The anti-malware solution(s):
- Performs periodic scans and active or real-time
scans.
OR - Performs continuous behavioral analysis of systems or processes.
3.2.1 - 5.3 Ensure that anti-virus mechanisms are actively running and cannot be disabled or altered by users, unless specifically authorized by management on a case-by-case basis for a limited time period.
Change: Reformulation.
4.0 - 5.3.5 Anti-malware mechanisms cannot be disabled or altered by users, unless specifically documented, and authorized by management on a case-by-case basis for a limited time period.
Change: Reformulation.
4.0 - 5.3.5 Anti-malware mechanisms cannot be disabled or altered by users, unless specifically documented, and authorized by management on a case-by-case basis for a limited time period.
3.2.1 - 5.4 Ensure that security policies and operational procedures for protecting systems against malware are documented, in use, and known to all affected parties.
Change: Reformulation.
4.0 - 5.1.1 All security policies and operational procedures that are identified in Requirement 5 are:
• Documented.
Change: Reformulation.
4.0 - 5.1.1 All security policies and operational procedures that are identified in Requirement 5 are:
• Documented.
- Kept up to date.
- In use.
- Known to all affected parties.
3.2.1 None
Change: NEW
4.0 - 5.1.2 Roles and responsibilities for performing activities in Requirement 5 are documented, assigned, and understood.
Change: NEW
4.0 - 5.1.2 Roles and responsibilities for performing activities in Requirement 5 are documented, assigned, and understood.
3.2.1 - None
Change: NEW
4.0 - 5.2.3.1 The frequency of periodic evaluations of system components identified as not at risk for malware is defined in the entity’s targeted risk analysis, which is performed according to all elements specified in Requirement 12.3.1.
Change: NEW
4.0 - 5.2.3.1 The frequency of periodic evaluations of system components identified as not at risk for malware is defined in the entity’s targeted risk analysis, which is performed according to all elements specified in Requirement 12.3.1.
3.2.1 - None
Change: NEW
4.0 5.3.2.1 If periodic malware scans are performed to meet Requirement 5.3.2, the frequency of scans is defined in the entity’s targeted risk analysis, which is performed according to all elements specified in Requirement 12.3.1.
Note: This requirement requires a target risk assessment to establish a frequency for traditional scanning. QSAs will want to see documented analysis within the TRA and the organizations’ ability to demonstrate the frequency stated has been followed.
Change: NEW
4.0 5.3.2.1 If periodic malware scans are performed to meet Requirement 5.3.2, the frequency of scans is defined in the entity’s targeted risk analysis, which is performed according to all elements specified in Requirement 12.3.1.
Note: This requirement requires a target risk assessment to establish a frequency for traditional scanning. QSAs will want to see documented analysis within the TRA and the organizations’ ability to demonstrate the frequency stated has been followed.
3.2.1 - None
Change: NEW
4.0 - 5.3.3 For removable electronic media, the anti- malware solution(s):
Change: NEW
4.0 - 5.3.3 For removable electronic media, the anti- malware solution(s):
- Performs automatic scans of when the media is inserted, connected, or logically mounted,
OR - Performs continuous behavioral analysis of systems or processes when the media is inserted, connected, or logically mounted.
- Modern anti-malware systems will perform behavioral analysis of any file executed regardless of storage location. Organizations must ensure that traditional anti-virus/malware systems are configured to immediately scan removable media when it is inserted or mounted.
- Most anti-malware solutions can be configured to scan removable media, though the functionality is usually disabled by default due to user experience implications; scanning a large USB drive with many files can take substantial time, and be quite inconvenient.
- Organizations using a continuous behavioral analysis of systems or processes when the media is inserted, connected, or logically mounted are not required to enable an automatic scan of media upon insertion, connection, or logical mounting.
3.2.1 - None
Change: NEW
4.0-5.4.1 Processes and automated mechanisms are in place to detect and protect personnel against phishing attacks.
Note:
Change: NEW
4.0-5.4.1 Processes and automated mechanisms are in place to detect and protect personnel against phishing attacks.
Note:
- These processes and mechanisms must be more than simple warnings about potential phishing. The requirement is for processes and automated mechanisms that cannot just detect phishing attempts but will actually protect end-users.
- This controls requires actions probably on email servers even if those are outside the PCI CDE. There are solutions out there today, and some cloud-based solutions like Gmail and Microsoft Defender for Office365 already have anti-phishing options included.
 RSS Feed
RSS Feed
